Cisco just released yesterday the latest version of the FirePOWER software IE Version 6.1. The release notes can be found HERE. This post will provide a first look and quick review of the upgrade process using the FirePOWER virtual manager.
My current lab has a ASA5506 managed by a virtual FirePOWER appliance. Both are running 6.0.1. Here is my 5506 managed by the virtual FirePOWER appliance.
 The first step for me to upgrade to 6.1 is to upgrade my FirePOWER manager. I downloaded the file Sourcefire_3D_Defense_Center_S3_Upgrade-6.1.0-330.sh and went to the GUI manager, clicked system -> updates and selected add upload update. I selected the upgrade file (little package image) and applied it to my manager.
The first step for me to upgrade to 6.1 is to upgrade my FirePOWER manager. I downloaded the file Sourcefire_3D_Defense_Center_S3_Upgrade-6.1.0-330.sh and went to the GUI manager, clicked system -> updates and selected add upload update. I selected the upgrade file (little package image) and applied it to my manager.
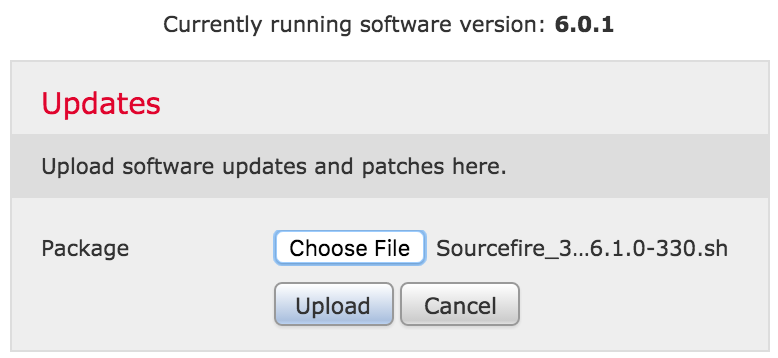 It took about 5 minutes to upload the upgrade file and about 2-3 hours to run the upgrade process ( I did it before I went to bed and checked it in the middle of the night). While checking the manager, I saw the following screen after an hour
It took about 5 minutes to upload the upgrade file and about 2-3 hours to run the upgrade process ( I did it before I went to bed and checked it in the middle of the night). While checking the manager, I saw the following screen after an hour
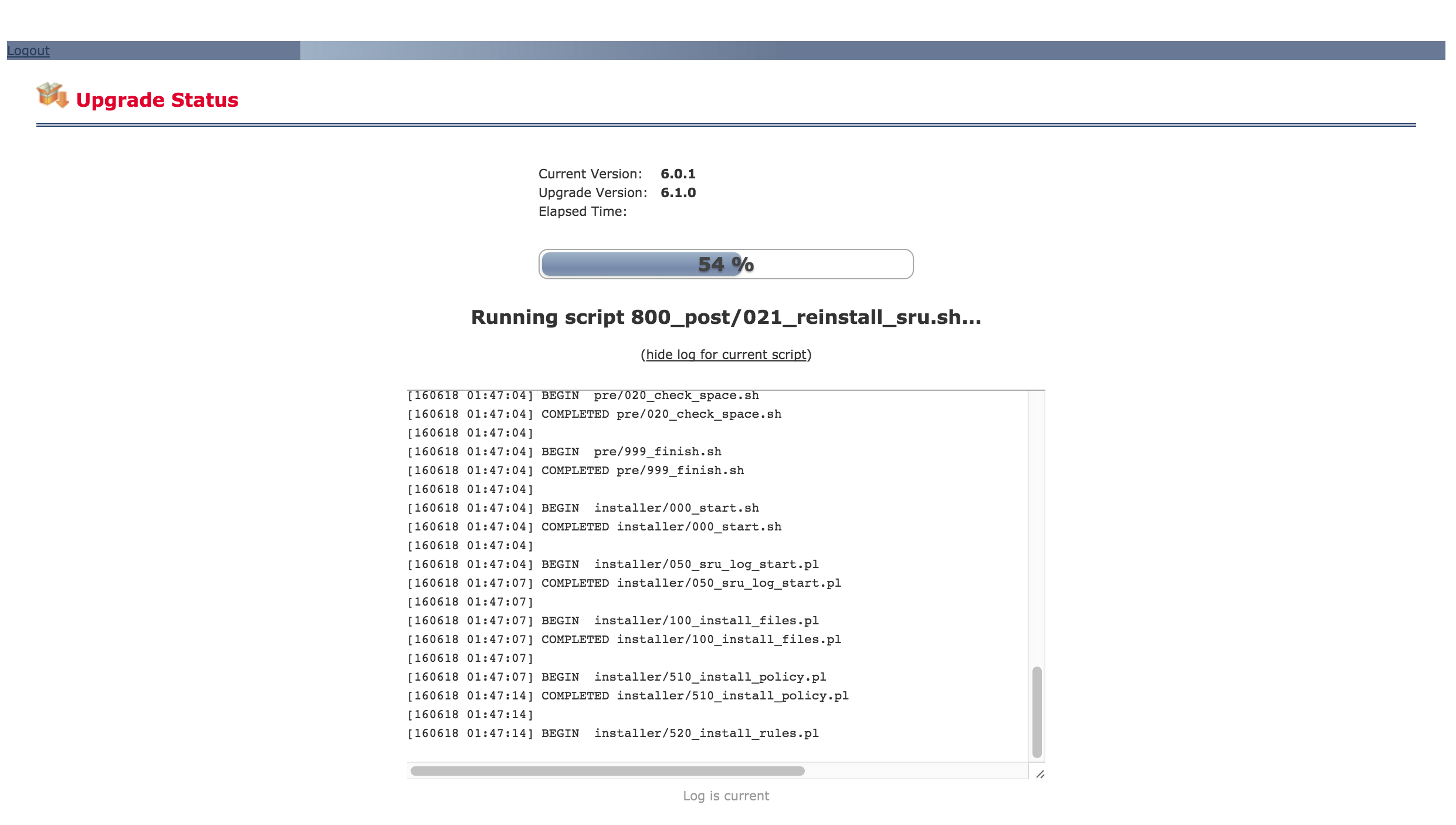 Once my manager was upgraded, I downloaded two files to upgrade my ASA5506. The first is a the Cisco_FTD_Upgrade-6.1.0-330.sh script and other is the upgrade utility . I tried running the upgrade directly a few times and it failed every time at the 20 minute point.
Once my manager was upgraded, I downloaded two files to upgrade my ASA5506. The first is a the Cisco_FTD_Upgrade-6.1.0-330.sh script and other is the upgrade utility . I tried running the upgrade directly a few times and it failed every time at the 20 minute point.
I found the fix was to delete the ASA from the Manager, log into the command line of the ASA and remove the manager using the command “configure manager delete”, then add the manager back in ASA CLI using the command “configure manager add X.X.X.X (special term), then add the ASA back to the FirePOWER manager. Once I had the FirePOWER showing the ASA correctly, applying the Cisco_FTD_Upgrade-6.1.0-330.sh worked. Note I did these steps AFTER I upgraded the FirePOWER manager. If you have trouble upgrading a FirePOWER appliance or ASA with FirePOWER, try removing and adding it!
The ASA5506 6.0.1 to 6.1 upgrade process took about two hours to complete. Once completed, it rebooted and I had everything at 6.1.
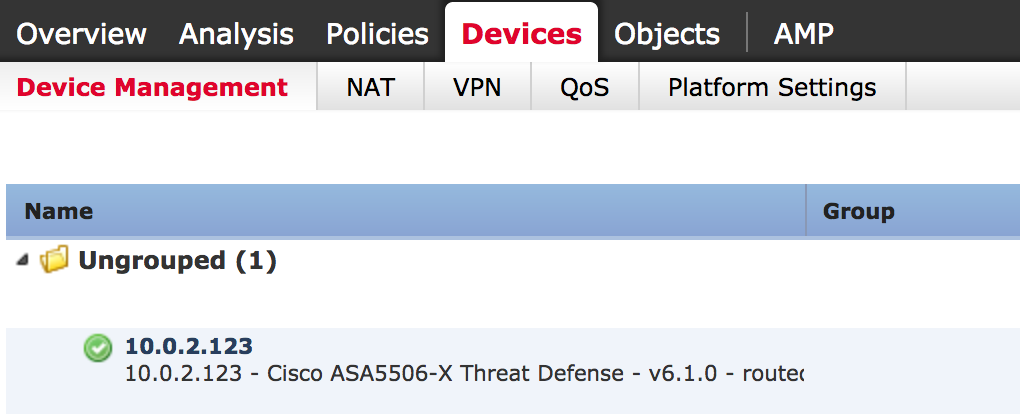 And that was all that was to that. Now here is a quick list of some of the new features.
And that was all that was to that. Now here is a quick list of some of the new features.
- A very cool and New On-Box Device Manager. I’ll be post more about this later this week since I”m using the centralized manager hence can’t pull that up without adding another ASA via separate manager. I’ve seen demos of it and its nice. More to come on that shortly.
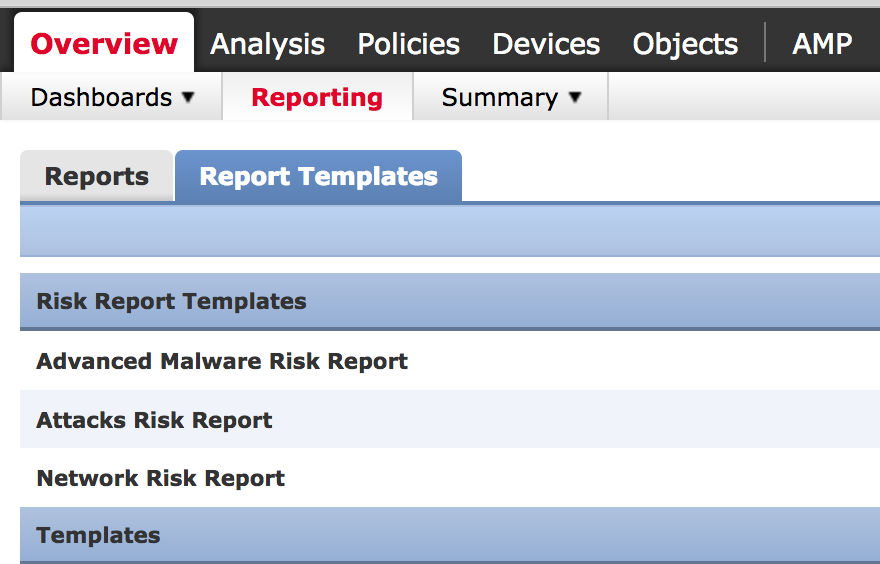
- Integrated Risk Reports – This use to be a script to see various risk reports. Now they are built into FirePOWER. Here is a screenshot of the three risk report templates

- High Availability for Firepower Management Center … kind of important.
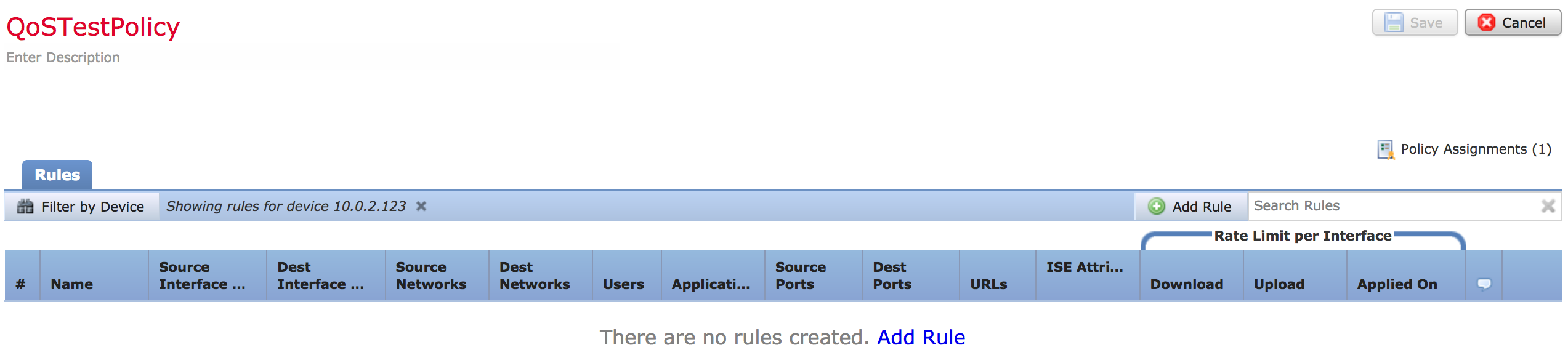
- Rate Limiting – Yeay finally! The ability to permit but limit a specific service. Here is a screenshot of the basic QoS Page. As you can see, the rate limiting stuff is to the right.

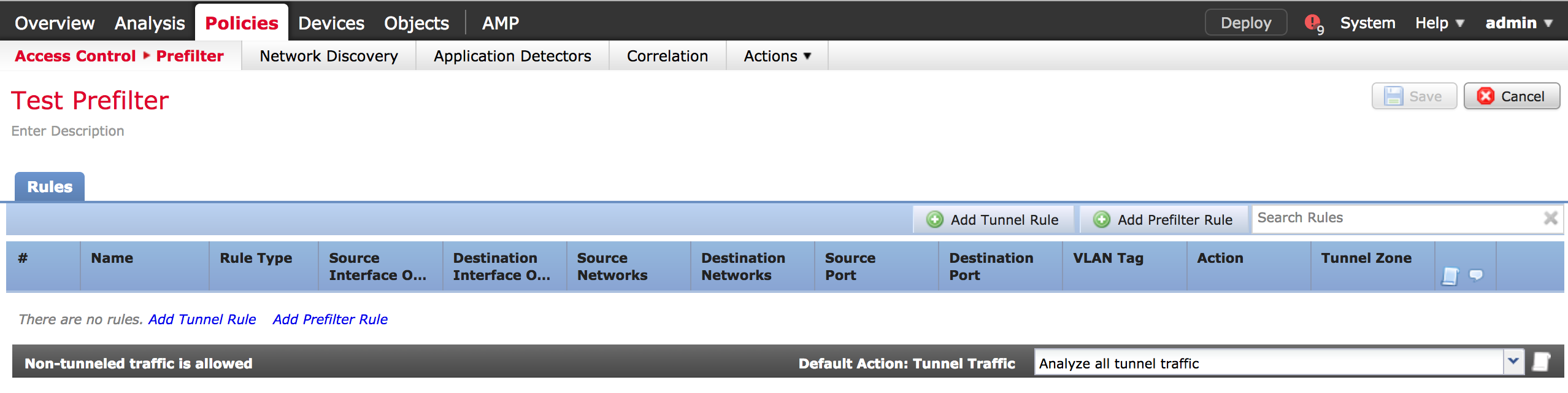
- Prefilter policies support the efficient flow of traffic. Here is a screenshot of the tunnel rule and prefilter rule options. It is configured like a access control policy.

- Site-to-Site VPN is now available
- Multicast Routing is now available
- VDI Identity Support – This one solves a identity gap. The problem was FirePOWER could only see the traffic within its vision meaning anything behind a NAT would be seen as one IP address. This new feature associates a user with a IP address and port range combination through the use of a new agent deployed on the Windows Terminal Server. The Cisco Terminal Services Agent intercepts logs and assigns port ranges to every user that logs in. This gives FirePOWER visibility of the actual port ranges of the users.
- SafeSearch / YouTube EDU Policies – Can support higher education needs for filtering searching.
- ISE Remediation – FirePOWER integration is now built int for auto remediation of threats.
- True-IP Policy Enforcement – As long as the proxy server supports the insertion of XFF headers into it, Firepower is now able to enforce policies based on the actual IP address.
- Inline SGT Tags – With Version 6.1, you can now configure inline Security Group Tag (SGT) policies that will read the SGT tag off of the packet and enforce the policy on the packet without requiring a connection to the ISE Server all the time.
- AMP Private Cloud with ThreatGrid
And many more … go check it out. I just finished the upgrade so I’ll play with it over the next week and post a more detailed 2nd look soon.




Nice article.
Can you send links to the On Box management Demo?
Thanks
Have you tried a new installation of defence center 6.1 on vmware? I my memory is correct the earlier versions suggested 250 gb of space but this release only recommended 50!? Thanks for a good site!
VDI Identity Support – Do you know where to get the new agent to be deployed on the Windows Terminal Server from?
Hello,
I’m wondering what your thoughts are on the need to do SSL scanning for Url filtering on the firepower module? I would like to use this for filtering K-12 schools and I’m getting mixed answers on the need to do SSL scanning of traffic with the next gen systems. The performance hit on our 5545 would be quite high if we decided to enable it and I didn’t want to have to do SSL scanning if it’s not necessary.
Hi Dan,
Well it depends on your concern and what you are trying to secure. The typical thought is the fear that an attacker would launch something over HTTPS, which is encrypted bypassing IPS detection. This would not apply to DNS or reputation security as well as things that evaluate what comes in such as breach detection technologies. The reality is many attackers are not attacking this way today because they don’t want to deal with certificates. Also another thing to consider is the type of traffic you would like to decrypt. Most organizations are using selective decryption meaning not decryption things like banking however focusing on social media.
Regarding Cisco’s capabilities, some technologies such as Firepower have a performance hit if SSL decryption is enabled. The newer hardware is built to accommodate that but it comes down to a simple concept. If you enable SSL decryption and decrypt traffic for any vendor, you are increasing the amount of traffic. If the hardware is not sized properly, things will slow down. The same effect happens if you run a gig against a 200 mg appliance. Methods to prepare for this are A) Using a load balance type technology such as F5 or A10, B) Enable SSL selectivity and when hardware is sized properly for it. C) Leverage cloud proxies or dedicated proxies for handling larger SSL performance needs. This again only applies to the need for having your IPS detect traffic. If you have reputation security limiting who you can communicate with or breach detection, those won’t be impacted by this. Examples of reputation would be your Firepower URL license and AMP would be a breach detection.
Hope this helps