Cisco’s research group Talos posted about their research on the Nuclear Exploit Kit HERE. They compare it to their research on Angler as well as break down the attack. Its a good read.
Talos is constantly monitoring the threat landscape and exploit kits are a constantly evolving component of it. An ongoing goal of Talos is to expose and disrupt these kits to protect the average internet user being targeted and compromised. We were able to gain unprecedented insight into Angler exploit kit and reveal details of the activity that were previously unknown. Now we have focused our attention on the Nuclear exploit kit with similar results.
Nuclear exploit kit has been steadily compromising users for years and has been effective in evolving as well as adding new exploits to their arsenal. However, it has been operating largely off the radar compared to some of the more prolific kits that are active today. This lack of deep visibility was one of the driving forces behind the deep investigation into its activity. What we found was a sophisticated threat that has been successfully targeting and compromising users in more than 10,000 different cities in more than 150 countries.
We continued digging through our data and wound up with a list of 10-15 IP’s that were hosting the Nuclear EK. This allowed us to focus on the providers hosting the activity. At this point the first key piece was identified: DigitalOcean. We were able to determine that practically all the Nuclear activity we were tracking was being hosted by DigitalOcean. Talos established contact with DigitalOcean and notified them of the activity and the details associated with the threat. DigitalOcean’s security team validated the malicious nature of the hosts and collaborated with Talos to provide valuable intel, during the take down, to help expose how the kit operates.
Provider Account Details
The question we posed ourselves was “How could this activity remain so well hidden from view?” and the answer was both obvious and surprising; Porn / Adult Entertainment websites. We started looking at the referers for this traffic and found almost half of the IP’s were directing from a single webcam ad that was hosted on a porn site, a censored version of which is found below. This cam ad was seen redirecting in excess of 25K IP’s to Nuclear in a single day. The use of the Spanish word “chicas”, in the bottom corner, leading to a theory that the kit was potentially targeting non-native English speaking countries.
This cam ad was seen redirecting in excess of 25K IP’s to Nuclear in a single day. The use of the Spanish word “chicas”, in the bottom corner, leading to a theory that the kit was potentially targeting non-native English speaking countries.
LANGUAGE DATA
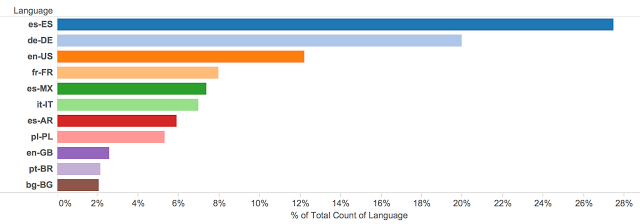 Unsurprisingly, English was not the most popular language header found in the data. Spanish and German were the most common languages followed by English with significant amounts of French, Italian, and Polish.
Unsurprisingly, English was not the most popular language header found in the data. Spanish and German were the most common languages followed by English with significant amounts of French, Italian, and Polish.We wanted to look at how this relates to the amount of native speakers globally. We found data from 2007 that showed that similar amounts of people in the world speak English (5.52%) and Spanish (5.85%) natively. German (1.39%) however had a quarter of the volume of native speakers of English and Spanish with French (1.12%), Italian (0.90%), and Polish (0.61%) having significantly lower native speaking populations than the other languages. Based on this information we decided to pivot on the IP’s affected and start trying to identify where the traffic was originating.
GEOGRAPHIC IP BREAKDOWN
Talos took the ~60K IP addresses and began tracking them based on basic geographic information like city and country of origin. The results backed up what we had already seen from the HTTP headers, discussed above, Spanish speaking countries made up a significant portion of the activity.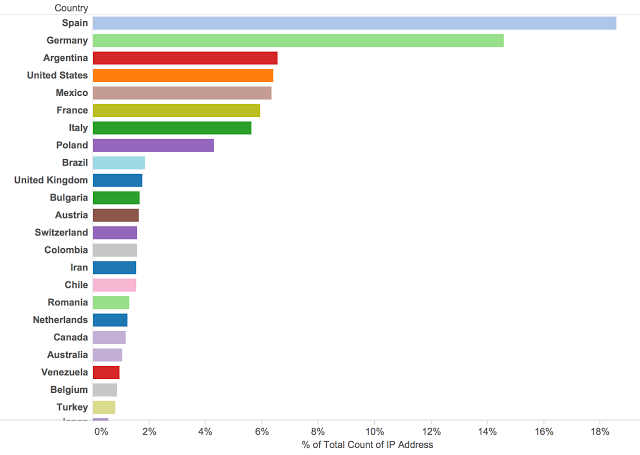 Spain was the largest target, accounting for almost 20% of the hosts that were interacting with this particular server. Germany was also responsible for ~15% of the potential victims. Notice that the United States was actually the 4th most victimized country with Mexico accounting for an almost equal share of hosts. This is one of the most telling distinctions from the geographic data since Mexico has a much smaller population of internet connected citizens when compared to the United States. Also, there are 41 million native Spanish speakers inside the United States, this could account for at least some portion of the United States based victims.
Spain was the largest target, accounting for almost 20% of the hosts that were interacting with this particular server. Germany was also responsible for ~15% of the potential victims. Notice that the United States was actually the 4th most victimized country with Mexico accounting for an almost equal share of hosts. This is one of the most telling distinctions from the geographic data since Mexico has a much smaller population of internet connected citizens when compared to the United States. Also, there are 41 million native Spanish speakers inside the United States, this could account for at least some portion of the United States based victims.
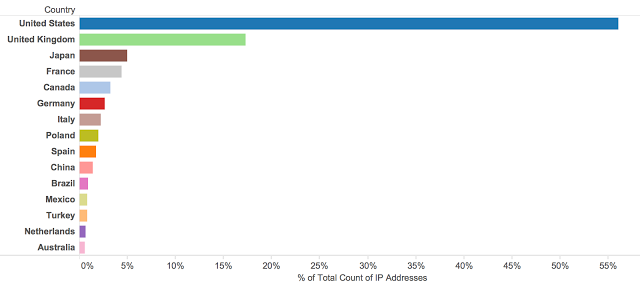 Almost 75% of the Angler victims were from the United States and the United Kingdom. Also of note was how few countries were involved. Angler’s victim base was from only 15 different countries. Nuclear’s reach was much wider with more than 100 countries seen sending traffic to the Nuclear server including a surprising amount from countries like Iran and Venezuela. Nuclear appears to be avoiding the United States and United Kingdom and focusing on drawing users in from elsewhere around the globe. As we’ve seen previously, other exploit kits like Angler have targeted English speaking countries heavily. It’s possible Nuclear was trying to avoid competition for users as well.
Almost 75% of the Angler victims were from the United States and the United Kingdom. Also of note was how few countries were involved. Angler’s victim base was from only 15 different countries. Nuclear’s reach was much wider with more than 100 countries seen sending traffic to the Nuclear server including a surprising amount from countries like Iran and Venezuela. Nuclear appears to be avoiding the United States and United Kingdom and focusing on drawing users in from elsewhere around the globe. As we’ve seen previously, other exploit kits like Angler have targeted English speaking countries heavily. It’s possible Nuclear was trying to avoid competition for users as well.The referers for the traffic were the next area we started looking at and the data again backed up what we had seen in the geographic breakdown. We found more than 7,500 unique referers in the data with the pornographic ad above accounting for a huge portion of the redirections (~45%). Also of note were the different TLDs that were found in the data. We found lots of TLDs associated with non-English speaking countries in Europe and other areas outside the US/UK. 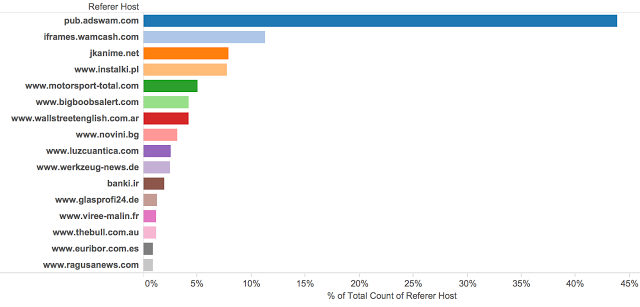 This could have been done through both compromised websites and malvertising. Based on the trends that we have been seeing both are being utilized at different times and this campaign looks to be heavily focused on malvertising.
This could have been done through both compromised websites and malvertising. Based on the trends that we have been seeing both are being utilized at different times and this campaign looks to be heavily focused on malvertising.
 This could be related to the relative lack of logging that was occurring on the proxy server itself. The proxy server had virtually all logging disabled on the system and was using a very similar NGINX configuration as we saw with Angler. Below is a copy of the NGINX configuration we found on the Nuclear server.
This could be related to the relative lack of logging that was occurring on the proxy server itself. The proxy server had virtually all logging disabled on the system and was using a very similar NGINX configuration as we saw with Angler. Below is a copy of the NGINX configuration we found on the Nuclear server.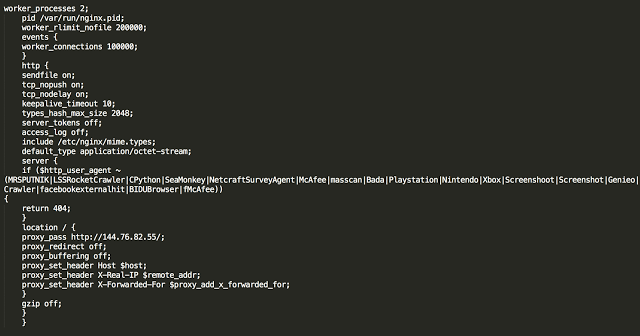 It does show the proxy configuration passing the traffic to the exploit server with the additional header data. However, there is also one key piece of information, some user agent checking. There is a list of keywords in a user agent that will result in the exploit kit returning a 404. The words that the kit is checking for are:
It does show the proxy configuration passing the traffic to the exploit server with the additional header data. However, there is also one key piece of information, some user agent checking. There is a list of keywords in a user agent that will result in the exploit kit returning a 404. The words that the kit is checking for are:
- MRSPUTNIK
- LSSRocketCrawler
- CPython
- SeaMonkey
- NetcraftSurveyAgent
- McAfee
- masscan
- Bada
- Playstation
- Nintendo
- Xbox
- Screenshoot
- Screenshot
- Genieo
- Crawler
- facebookexternalhit
- BIDUBrowser
- fMcAfee
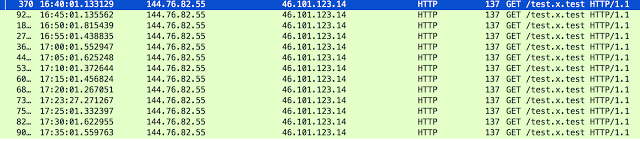
 This is an interesting health monitoring flow since it originates from the exploit server to the proxy server, which in turn directs it to the exploit server getting a response. Below is a sample of the actual traffic that was returned.
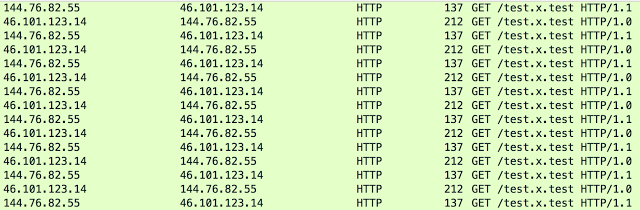
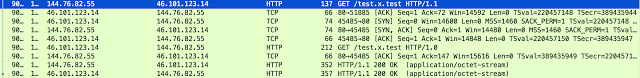
This is an interesting health monitoring flow since it originates from the exploit server to the proxy server, which in turn directs it to the exploit server getting a response. Below is a sample of the actual traffic that was returned.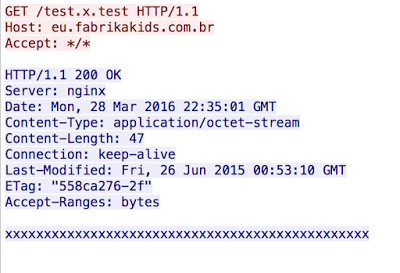 Each time the server would respond with 47 x’s. This circular data flow served as a health monitoring capability, however we did not find any evidence of remote logging being done from other servers. There is one other odd behavior, different HTTP versions being utilized for the back-end communication. All the requests coming to the proxy server were using HTTP/1.1 which is standard for web traffic. However, the traffic from the proxy server to the exploit server was using HTTP/1.0. Below is an example from the health monitoring requests.
Each time the server would respond with 47 x’s. This circular data flow served as a health monitoring capability, however we did not find any evidence of remote logging being done from other servers. There is one other odd behavior, different HTTP versions being utilized for the back-end communication. All the requests coming to the proxy server were using HTTP/1.1 which is standard for web traffic. However, the traffic from the proxy server to the exploit server was using HTTP/1.0. Below is an example from the health monitoring requests.