I see a lot of hesitation from administrators when having a conversation about cloud based security. People seem to be uneasy with the idea of having anything security related managed outside of their company walls. Some administrators express concerns that there is a potential weakness opening up a connection from their inside network to the cloud (even though it is encrypted) while others feel uneasy about having people outside their staff accessing equipment for maintenance or other purposes. I’ve also had the question “what happens if a client sharing a security device in the cloud gets compromised? Will that impact our business”? (I’ve never heard of this happening and there are hundreds of cloud offerings available today). These are just a few concerns that gives cloud based security a bad reputation before it is evaluated for its true potential.
Cloud Security should be looked at as a method of outsourcing security. Why would you want to do this? There are many benefits and for some situations such as locations spread across the world, cloud is the only feasible answer. Here are some of the top benefits of going cloud based security.
- Maintenance – Cloud solutions are updated in the cloud. This means you don’t have to manage security patches, updates, etc. as well as deal with “maintenance windows” to take the system down for updates. Not dealing with this equals savings in manpower as well as always having the latest updates.
- Scalability – Cloud based security typically requires a connector between the LAN and cloud or low cost hardware onsite. That connector is easier to deploy than an on premiums security product making scaling across multiple locations cost effective. Think about a retail store chain of 200 locations desiring the same level of security. Is it more cost effective to deploy and maintain 200 high-end security products or just connect them to a cloud based offering?
- Deployment – Cloud based security products can typically be configured prior to implementation meaning you can do a lot of the legwork upfront via the cloud management interface. Appliance based technically typically needs to be setup in a lab prior to going live. With most physical products, you have to connect to a management port to get a local IP address, do some basic setup, upgrade software and then start configuring the solution.
- Mobile – Cloud technologies can be accessed anywhere meaning many offerings can be agents that always enforce security regardless of the user’s location. This makes protecting global road warriors a lot easier than hardening their laptops or forcing remote traffic from far away through a VPN just to run it through security filtering.
- Consistency – One difficult task to accomplish is enforcing a consistent security policy over multiple locations. One change such as updating a firewall rule means making sure each location has the capabilities to support the change as well as implementing the change. Cloud based offerings typically can centralized policies regardless the number of locations and deliver a consistent level of security.
- Cloud Based Intelligence – Many new security features are based upon cloud security intelligence meaning sampling larges amounts of data. Examples of this are website reputation (more found HERE), data behavior monitoring, etc. Some of these security features require data in the cloud to be effective.
There are different options for cloud security. In the Cisco world, Meraki represents the “cloud managed solutions” meaning you setup everything in the cloud and use physical appliances at each location. So using Meraki means you are outsourcing the management but own the enforcement points. Setup is plug and play meaning you configure everything from the cloud and plug in the appliances to a active port so they can download their configuration rather than accessing hardware locally. Meraki offers switches, security appliances, wireless access points, mobile device management applications and more.
Regardless of what Meraki product you own, you go to meraki.cisco.com to log into your main management interface.
Here is an exampling showing all devices on a network and a break down of how each device is impacting the network. You can click the applications chart to dive deeper into what websites people are accessing. 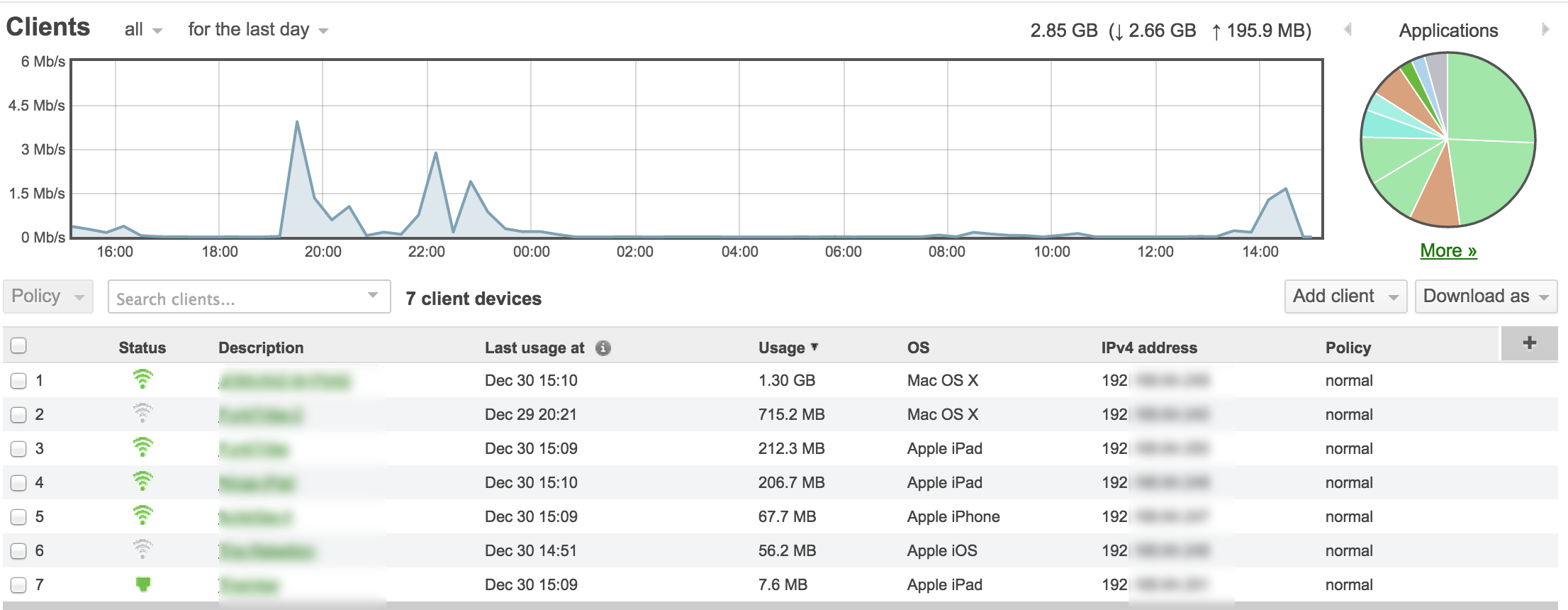 Here are some of the security options offered by Meraki. As expected, the typically features are available such as firewall, content filtering, IPS (powered by Sourcfire) and access control.
Here are some of the security options offered by Meraki. As expected, the typically features are available such as firewall, content filtering, IPS (powered by Sourcfire) and access control. 
Cisco also offers full blown cloud based security services known as Cisco’s Cloud Web Security (CWS). CWS is a series of service towers located all over the world that offer Application Visibility and Controls, Content Filtering, Anti-virus / malware / IPS and Day zero detection using a blend of behavior and file based services. CWS is similar to Ironport Web Security Appliance (WSA) however offered as a cloud service. Customers connect or route traffic from their gateway to the closet tower using ISR routers, Cisco ASAs, Cisco WSAs or the Anyconnect agent install on host devices. I find many of my customers have small branch offices with a switch and ISR router onsite so having the option to proxy traffic through the cloud rather than deploying another piece of hardware is critical for this situation.
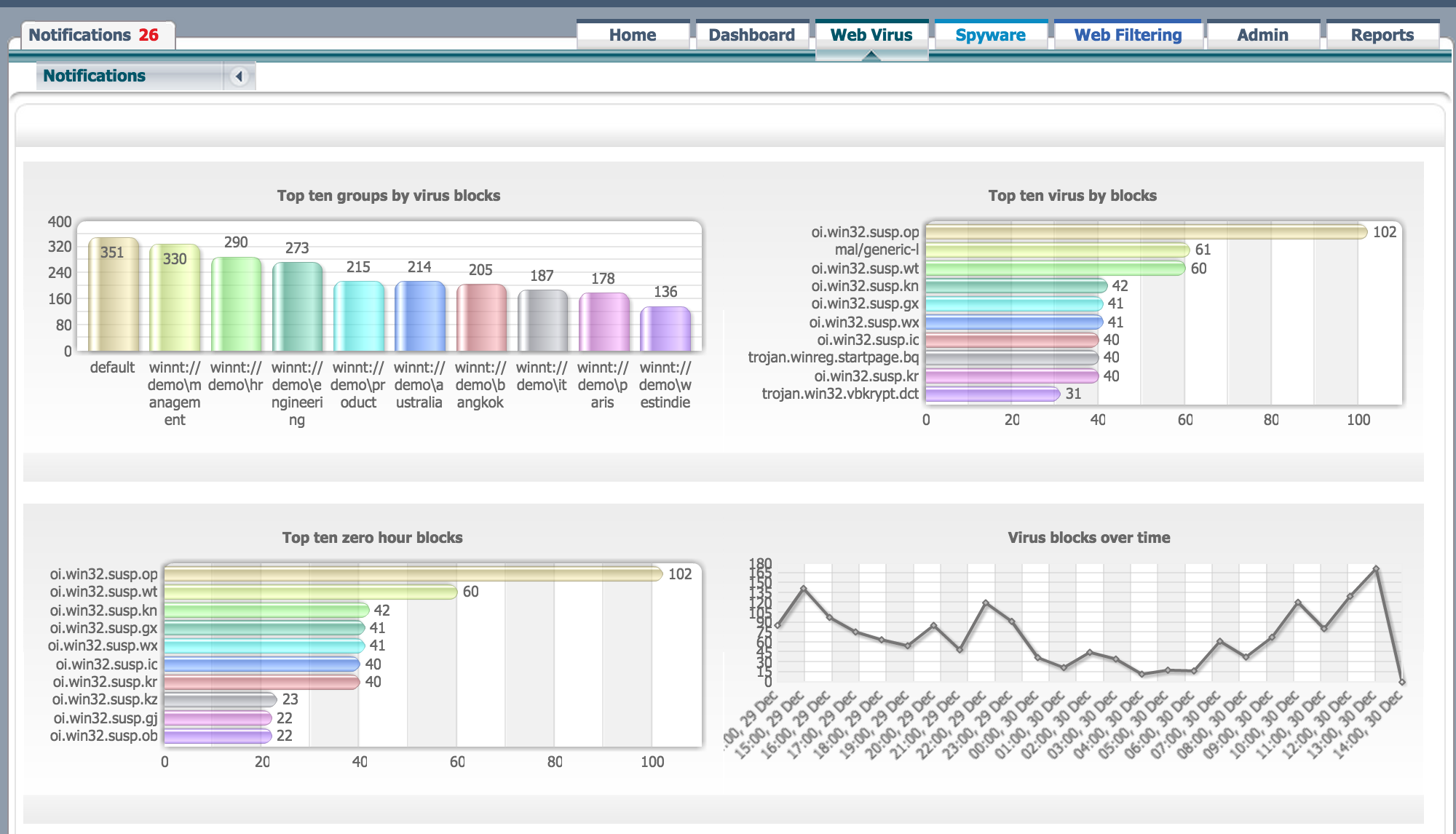
Here is an example of viewing viruses blocked by CWS
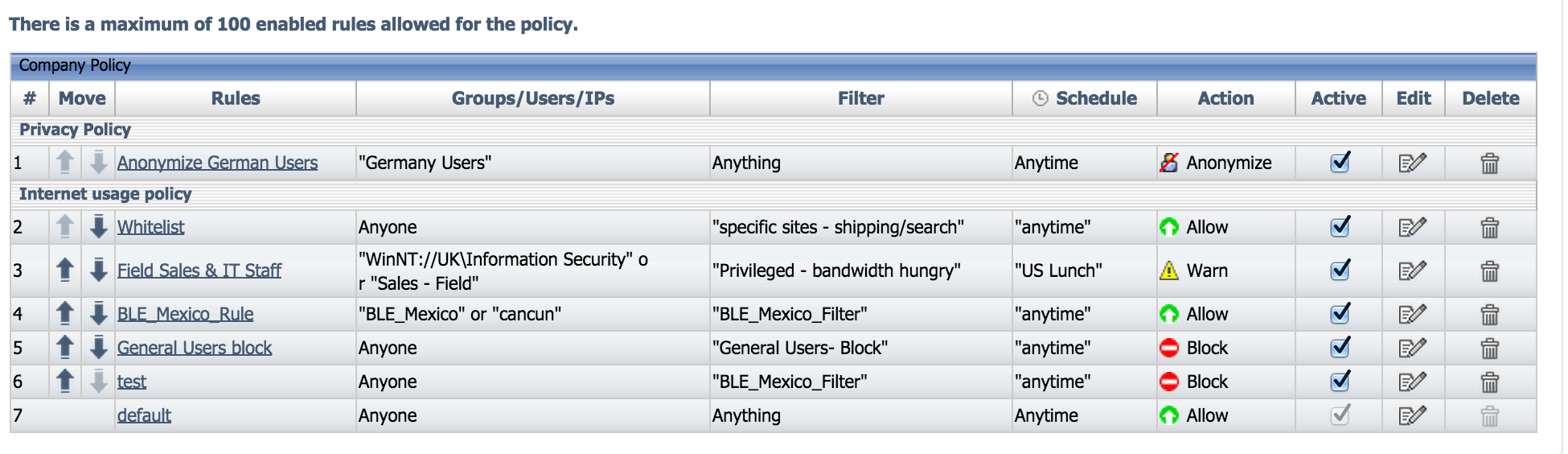
Here is an example of some content filter policies in CWS.
Cloud doesn’t have to be a all or nothing. Sometimes people consider a hybrid approach meaning keep certain things such as headquarter based security local while connecting smaller locations or remote users to a cloud offering. Another example of a hybrid use case is when a local security solution is being over utilized so part of the solution is outsourced via connecting it to the cloud (example sending web filtering to the cloud when a firewall with content control capabilities is being hammered).
There are disadvantages to cloud based security. Here are a few to consider
- Typically cloud based security has a higher cost than owning hardware since you are outsourcing maintenance and other services. This is not always the case however usually full blown cloud will cost more since it is a service.
- Most cloud security solutions can only see what is proxied through them. There are exceptions when cloud solutions offer network taps however typically on premiums appliances can see more inside network traffic while cloud technology can only see what is sent to the cloud.
- Sometimes security is required even when the network is down. If you are using a cloud based solution and the network is down, most likely the security part will fail open or use the last known configuration. This is not always the case however something to consider.
- Cloud based products tend to have a mandatory subscription depending on the offering. If this subscription runs out, the product is no longer effective. The same can be said about any licensed based product.
Hopefully this helps clear up some confusion with understanding the value of using cloud based security products.