Lancope is a NetFlow based tool that can turn your network into a gigantic sensor grid. This includes routers, switches, wireless access points, virtual systems aka servers in your data center and so on. So rather than having a handful of security tools looking for threats, your entire network takes part in your security defense against cyber attacks. I’ve wrote about Lancope HERE as well as how to build your own Lancope lab HERE.  The Lancope team runs a blog found HERE that has provided posts about using their solution to identify the latest cyber attacks. Some interesting articles recently posted focus on threats like Heartbleed, Putter Panda and Saffron Rose.
The Lancope team runs a blog found HERE that has provided posts about using their solution to identify the latest cyber attacks. Some interesting articles recently posted focus on threats like Heartbleed, Putter Panda and Saffron Rose.
The Heartbleed article was interesting based on how the Heartbleed vulnerability doesn’t leave forensic evidence on a vulnerable server’s logs meaning you can’t check if you have been breached.This is a huge concern since this vulnerability has been in the wild for many years prior to its announcement. This is bad news for most administrators since they can only assume the worst case if they find they have been vulnerable to this attack. Lancope however has shown there is a way to detect if there has been a breach using historic NetFlow data (more on that found HERE).
The Lancope team posted about a customer who used NetFlow data to identify a Heartbleed attack back in November 2013. The concept is as long as NetFlow is collected, certain searches can identify Heartbleed behavior such as multiple heartbeat requests or receiving more data than expected from a request. These are explained by these bullet points.
- “Attacks that target the Heartbleed vulnerability involve repeatedly issuing a specific request that produces a response that has the same size every time”
“Attacks that target Heartbleed are also likely to produce long flows. The reason that long flows come into play is that every Heartbleed transaction reveals to the attacker a new piece of data from the server’s memory”
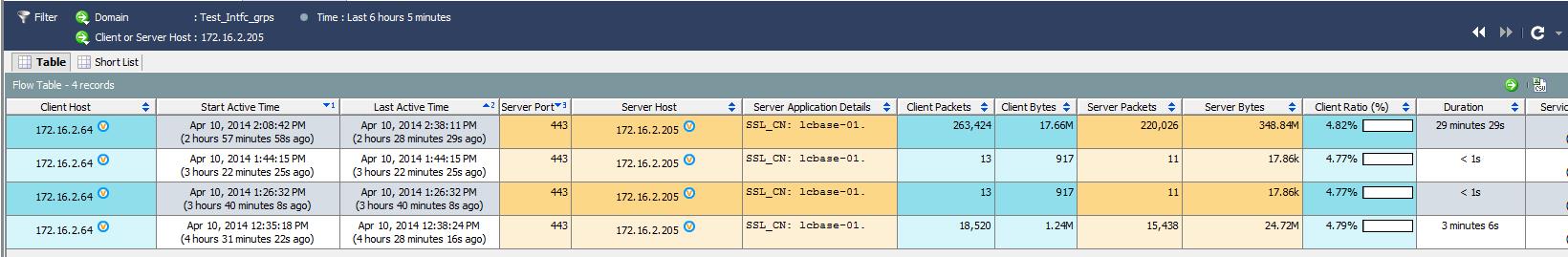 Lancope showing a possible Heartbeat breach
Lancope showing a possible Heartbeat breach
Steps for searching archived NetFlow in Lancope can be found HERE. This is useful for identifying various threats and can include building alarms to be triggered if future attacks are detected.
Putter Panda is a cyber espionage group that conducts operations from China and likely doing so on behalf of the Chinese People’s Liberation Army (PLA). They have targeted U.S. government groups, research, technology and other agencies using exploits in popular applications making their breaches difficult to detect. Once exploited, victim systems are rooted with remote access tools providing the Putter Panda hackers inside access to the target network. Lancope wrote about hunting Putter Panda attacks HERE.
The Putter Panda use case is interested because the concept is authorized systems are becoming doorways for outsiders and bypassing most popular security defenses. NetFlow can show that a sales person is doing reconnaissance aka running scans across the network for the first time, which is a common first step for a hacker to identify the new unknown environment. NetFlow can also show a system accessing other systems for the first time such as logging into a email server to possibly create fake accounts for future social engineering attacks. Many breaches include passing rootkits or malware, which not only beacon off new behavior that can be detected, but also can spread to other systems that eventually will also beacon in a similar method helping administrators detect all compromised systems without knowing what the exact threat is.
The Ajax Security Team was recently in the news for a cyber espionage campaign known as Operation Saffron Rose. This group uses multiple forms of web based attacks such as DDoS and Social Engineering with the goal of hurting a target’s reputation and stealing data. This example is similar to Putter Panda regarding breaching trusted systems to gain internal access and bypass common security defenses. The form of exploitation doesn’t matter since the compromised systems will act differently and set off alarms in behavior tools such as Lancope. This includes people clicking the wrong thing during a phishing campaign or systems seeing a ton of suspicious traffic during a DDoS attack as explained in the Saffron Rose post on the Lancope blog.
The Lancope blog has many other examples of detecting attacks such as BlackPOS, Operation SnowMan and so on. Check out their blog at http://www.lancope.com/slic/blog.


