There is a new ransomware slamming systems across the globe. Some have tagged it Petrwrap or GoldenEye. Cisco’s research team is calling it Nyetya. Whatever you want to call it, its pretty bad. Particularly, it seems to be pretty effective at spreading laterally. Everything isn’t know about this yet so check out the Cisco talos post HERE to stay up to date. Below is the latest research from Talos. Again, that post can be found HERE.
Update 2017-06-27 6:00pm EDT: Updated to include some of the technical functionality for the ransomware component of this attack.
| Screenshot of a system compromised by Nyetya. |
Since the SamSam attacks that targeted US healthcare entities in March 2016, Talos has been concerned about the proliferation of ransomware via unpatched network vulnerabilities. In May 2017, WannaCry ransomware took advantage of a vulnerability in SMBv1 and spread like wildfire across the Internet.
Today a new malware variant has surfaced that is distinct enough from Petya that people have referred to it by various names such as Petrwrap and GoldenEye. Talos is identifying this new malware variant as Nyetya. Our current research leads us to believe that the sample leverages EternalBlue and WMI for lateral movement inside an affected network. This behavior is unlike WannaCry, as there does not appear to be an external scanning component. Additionally, there may also be a psexec vector that is also used to spread internally.
The identification of the initial vector has proven more challenging. Early reports of an email vector can not be confirmed. Based on observed in-the-wild behaviors, the lack of a known, viable external spreading mechanism and other research we believe it is possible that some infections may be associated with software update systems for a Ukrainian tax accounting package called MeDoc. Talos continues to research the initial vector of this malware.
Snort rules that detect attempts to exploit MS17-010 have been available since April of 2017. Additionally, Talos has blacklisted known samples of this new ransomware variant in AMP.
MALWARE FUNCTIONALITY
In our investigation into this ransomware variant, Talos observed that compromised systems have a file named “Perfc.dat” dropped on them. Perfc.dat contains the functionality needed to further compromise the system and contains a single unnamed export function referred to as #1. The library attempts to obtain administrative privileges (SeShutdowPrivilege and SeDebugPrivilege) for the current user through the Windows API AdjustTokenPrivileges. If successful, the ransomware will overwrite the master boot record (MBR) on the disk drive referred to as PhysicalDrive 0 within Windows. Regardless of whether the malware is successful in overwriting the MBR or not, it will then proceed to create a scheduled task via schtasks to reboot the system one hour after infection.
As part of the propagation process, the malware enumerates all visible machines on the network via the NetServerEnum and then scans for an open TCP 139 port. This is done to compile a list of devices that expose this port and may possibly be susceptible to compromise.
The malware has three mechanisms used to propagate once a device is infected:
- EternalBlue – the same exploit used by WannaCry.
- Psexec – a legitimate Windows administration tool.
- WMI – Windows Management Instrumentation, a legitimate Windows component.
These mechanisms are used to attempt installation and execution of perfc.dat on other devices to spread laterally.
For systems that have not had MS17-010 applied, the EternalBlue exploit is leveraged to compromise systems. We have written about this previously in our coverage of WannaCry.
Psexec is used to execute the following instruction (where w.x.y.z is an IP address) using the current user’s windows token to install the malware on the networked device. Talos is still investigating the methods in which the “current user’s windows token” is retrieved from the machine.
C:\WINDOWS\dllhost.dat \\w.x.y.z -accepteula -s -d C:\Windows\System32\rundll32.exe C:\Windows\perfc.dat,#1
WMI is used to execute the following command which performs the same function as above, but using the current user’s username and password (as username and password). Talos is still investigating how the credentials are retrieved from the machine at this time.
Wbem\wmic.exe /node:"w.x.y.z" /user:"username" /password:"password" "process call create "C:\Windows\System32\rundll32.exe \"C:\Windows\perfc.dat\" #1"
Once a system is successfully compromised, the malware encrypts files on the host using 2048-bit RSA encryption. Additionally, the malware cleans event logs on the compromised device using the following command:
wevtutil cl Setup & wevtutil cl System & wevtutil cl Security & wevtutil cl Application & fsutil usn deletejournal /D %c:
COVERAGE
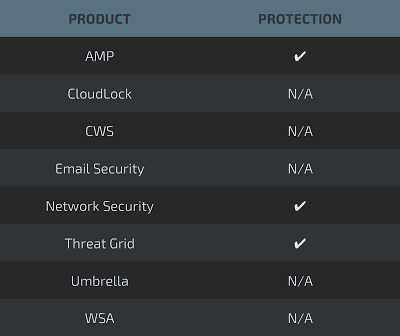
Network Security appliances such as NGFW, NGIPS, and Meraki MX can detect malicious activity associated with this threat.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Email and web has not been identified as an attacker vector at this time. Additionally, there are no known C2 elements related to this malware at this time.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
NGIPS / Snort Rules
The following NGIPS / Snort rules detect this threat:
- 42944 – OS-WINDOWS Microsoft Windows SMB remote code execution attempt
- 42340 – OS-WINDOWS Microsoft Windows SMB anonymous session IPC share access attempt
The following NGIPS / Snort rules are also indicators of infection traffic:
- 5718 – OS-WINDOWS Microsoft Windows SMB-DS Trans unicode Max Param/Count OS-WINDOWS attempt
- 1917 – INDICATOR-SCAN UPnP service discover attempt
- 42231 – FILE-OFFICE RTF url moniker COM file download attempt
- 5730 – OS-WINDOWS Microsoft Windows SMB-DS Trans Max Param OS-WINDOWS attempt
Threat Grid
Threat Grid is capable of detecting malware samples related to Nyetya as malicious.

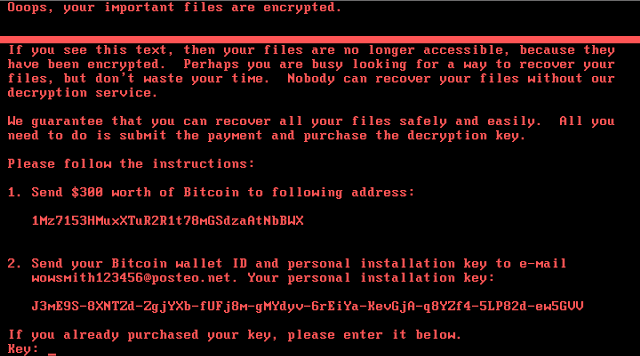
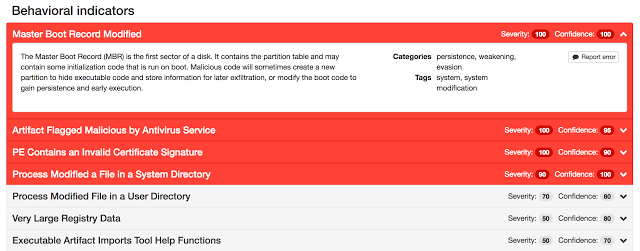




It is the duty of OS developers that they ensure security against all Ransomware attacks. They have left flaws within the systems that give rise to such issues. Whenever the security of system gets compromised, the users are left with either washing their entire hardware, or paying ransom to these bad guys. Both these solutions are very costly. DIY kind of stuff is not good either because it can cause further damage to the data files.