The 13th edition of the Verizon Data Breach Investigations Report is now out. You can download it at https://enterprise.verizon.com/resources/reports/dbir/. I thought I would give a quick overview of what I took away from it.
First off, here are my quick thoughts on the DBIR findings.
- The split between external to internal actors was 70/30: That’s pretty interesting to see 30% of the breaches were internal. I find many organizations lack insider threat detection.
- Hacking made up 45% of the attacks, 22% were social and 8% were malware related. To me, this once again shows the importance of both a vulnerability management program and a configuration management program. It seems like many organizations don’t focus hard enough on these topics while they are hyper focused on defending against malware.
- Almost half of the hacking attacks were related to brute-forcing passwords or exploiting web applications. Many organizations lack web application layer firewalls (WAFs), yet application hacking was a top hacking target. Password policies continue to become less effective and this report shows the result of that.
- 81% of breaches were contained within days or less. That’s pretty good compared to older breach reports.
- 72% involved large business victims. This is interesting as some reports will say small business is the top target for cyber threats based on the assumption they have less security than large business. The report also stated 86% of attacks were financially motivated, which makes sense why larger businesses would be the prime target.
- 27% of attacks were Ransomware. Some people have asked me if ransomware is no longer a thing. 27% is a pretty high number so yea, it’s still a thing.
- 37% stole user credentials. I recently saw a talk showing the latest research for brute-forcing passwords. Passwords are becoming easier to figure out yet people are using the same password tactics. I bet this number goes up next year. People really need to invest in multi-factor authentication.
The following diagram shows some interesting trends from the DBIR.
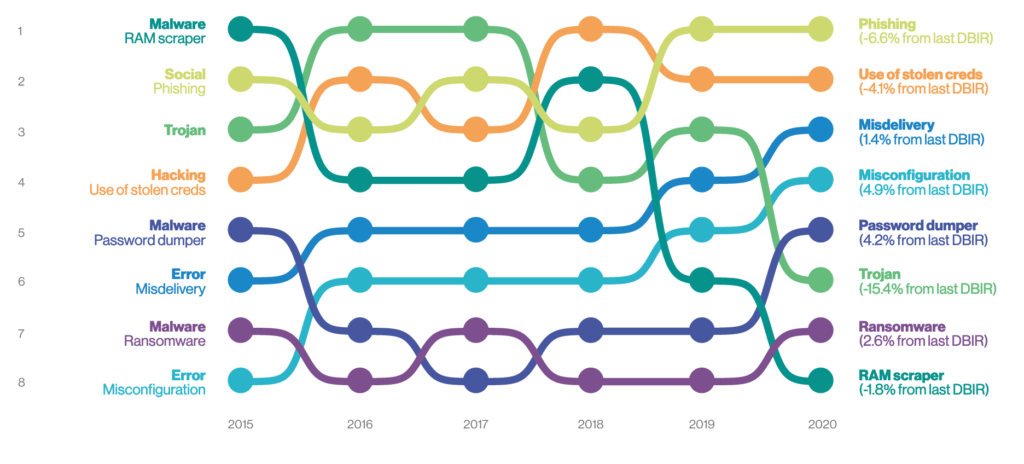
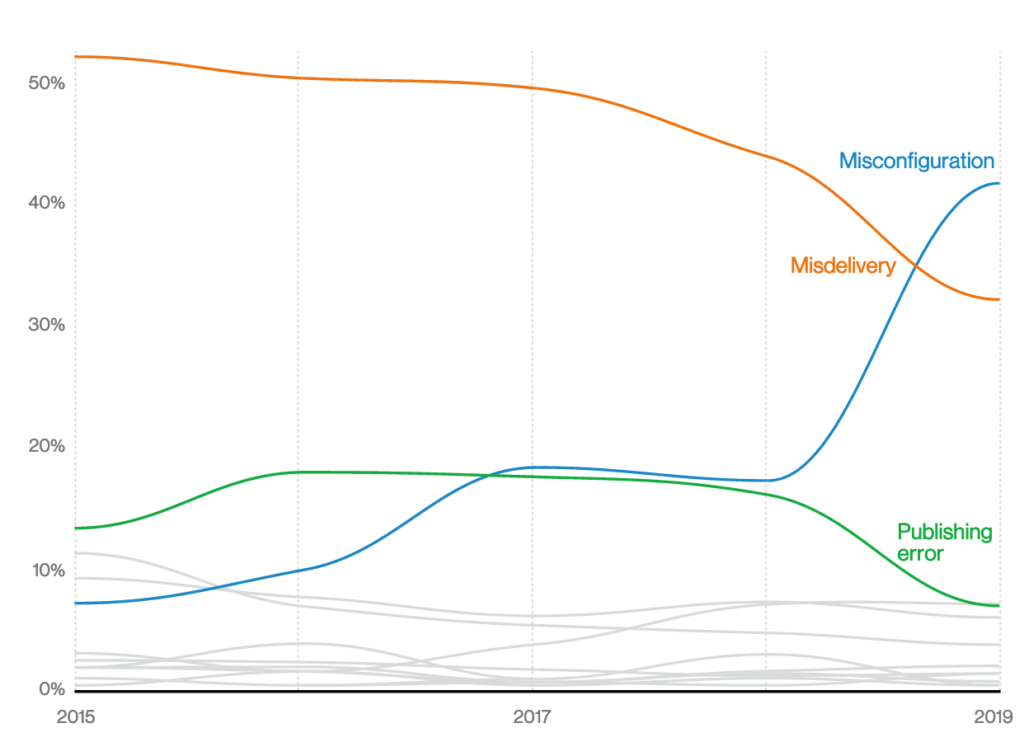
Misconfiguration is up, representing the need for patch management controls, enforcing proper configuration management and a strong vulnerability management program. According to this report, errors are more common than malware. Organizations need to take configuration management, patch management and other operation best practices more seriously. The next diagram shows the huge increase in errors this past year.
Ransomware is up 2.6% showing ransomware is not going away anytime soon. Ransomware, however, was not the top malware. Password dumping was the top malware. Email links are also a top threat meaning people clicking the wrong link within an email. I see malicious email links and password dumping as having similar outcomes. Many malicious links are designed to either exploit vulnerabilities with the goal of dropping malware on a system or tricking a user to enter their login credentials into a fake website. It is possible the malware that is dropped attempts to capture credentials linking these attack tactics. My recommendation is to ensure a solid email security solution is in place as well as reputation security both on the web and within the email scanning capability. Remember that a link to a malicious source within an email is actually a web problem. Validating the sources that you can communicate using reputation security reduces the threat of users clicking the wrong link, ransomware performing asymmetric encryption, and other threats. I wrote about reputations security HERE.
Other forms of malware are the usual suspects including trojans, droppers, and malware that exploits vulnerabilities. Crypto mining malware made up a small percentage, which the report points out could be due to these attacks only involved in smaller breaches that didn’t make the report’s interest requirements. Is crypto mining still a thing? Sure, but according to this report, there are probably bigger threats to be concerned about.
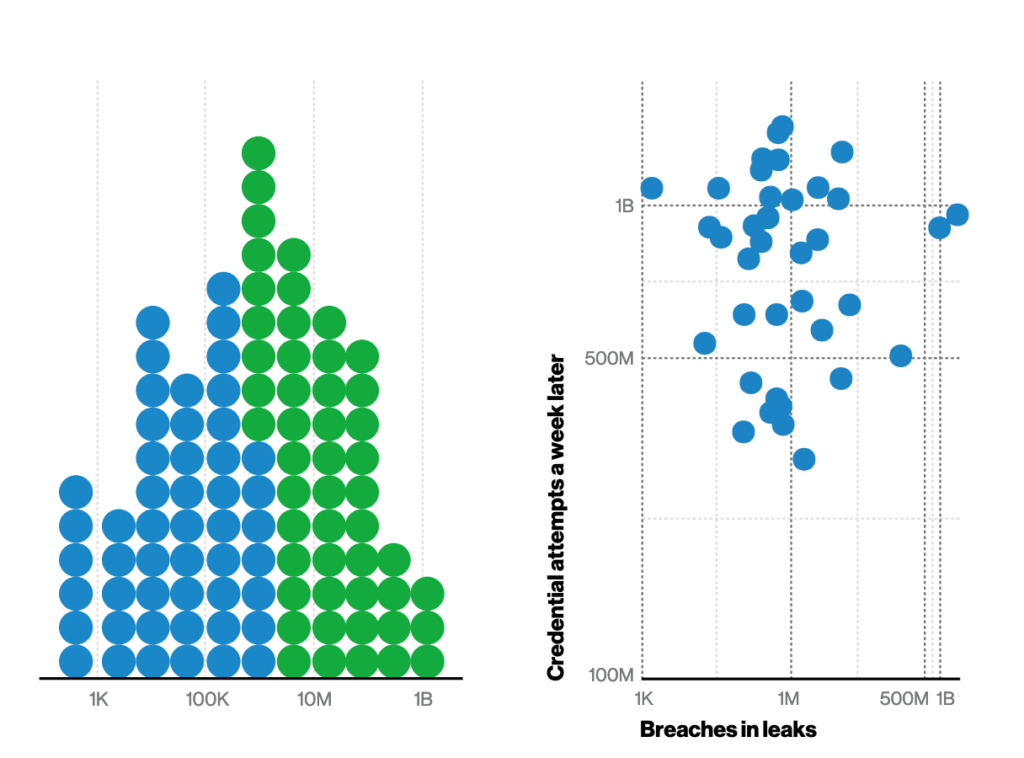
The following figure shows a massive increase in brute force attacks. Password policies need to improve as brute force tactics become more effective. Using real words in a password can easily be brute-forced. Also, using a special character at the beginning or end doesn’t add much value. My advice is to use a special character somewhere in the middle as well as use passphrases that are the first letter of each word so the result password is not a word found in any brute force dictionary. I also heavily advise using multi-factor authentication as well as ensure applications ask users to log-in verse performing a one-time login and granting access to everything. This recommendation follows the latest Zero Trust guidelines. Limit single-signon to none buisness essential applications.
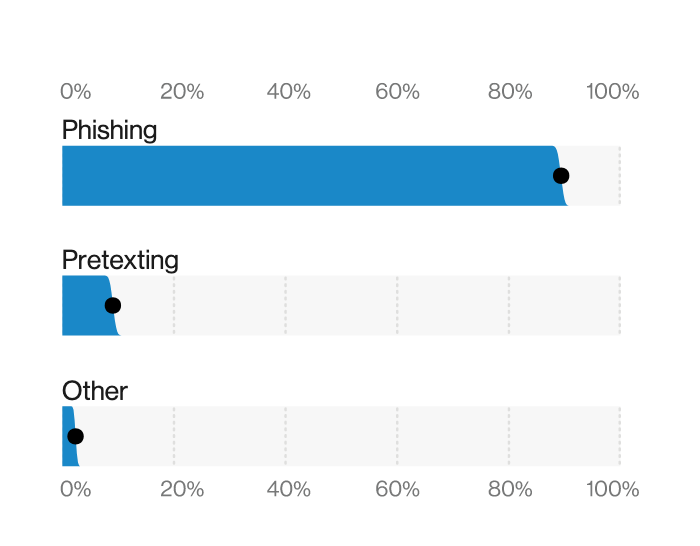
Phishing is very high, which makes sense as phishing is related to emails with malicious web links. This concept from the report should be a reminder about the importance of user training for phishing. Every organization should be testing users with fake phishing emails to ensure everybody is aware and looking for phishing within the email and social media. Tools such as the social engineering toolkit (SET) can be used to build a phishing campaign.
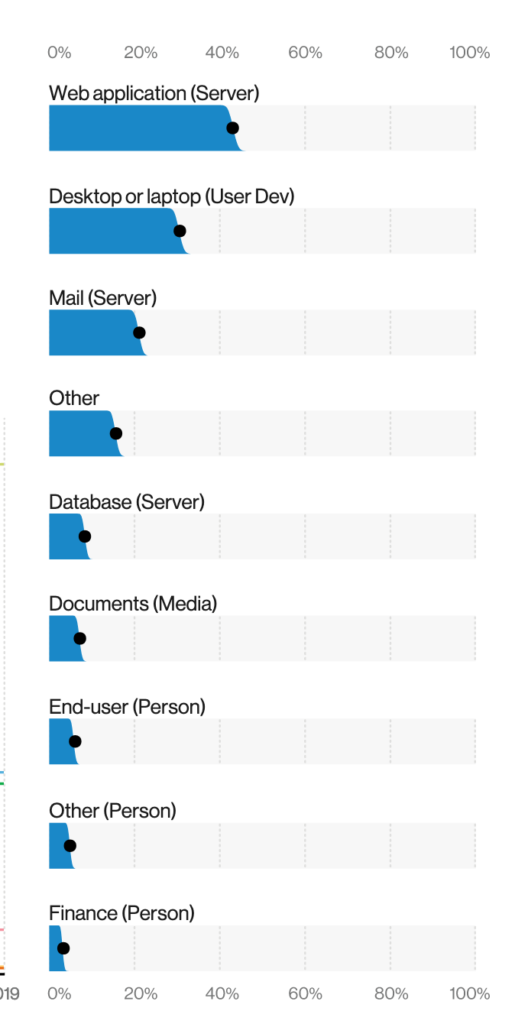
The final interesting data point I’ll dive into is the focus on web applications. Many organizations run web applications yet they have not invested in a web application firewall. Next-generation / application layer firewalls are good but they don’t defend against most web application threats such as SQL injection and cross-site scripting. As a result, organizations deploy application layer firewalls with a false sense of security regarding their web applications. The following images from the DBIR shows web applications as the top target for attack. I can hear the all stat guy asking you “Are you in good hands?” meaning are your web applications properly protected?
There are many other interesting data points within this years report including how each industry was impacted by the topics I covered. Make sure to download and check it out. Its free and extremely useful to understand the current threat landscape.




