I have recently seen a uptick in DDoS / DoS attacks against my customers and asked questions such as “how easy is it to perform these attacks?”, “who launches these attacks?” and “how can I defend against such attacks?”. I have spoke about this topic in the past however will provide both the executing and defending side of DoS in this post.A Denial of Service attack basically comes down to stopping a system or service from functioning. This can be accomplished through many methods ranging from compromising servers to disrupting a core component such as a network gateway. In general, there are two areas you will see these attacks, which are External and Internal. The most common from of external DoS is through overloading a target with many machines typically through a Botnet or remotely controlled army of computers. The term DDoS references this distributed concept covered in this post HERE. Internal attacks range from sending malformed traffic at a router to exploiting weaknesses in systems. Terms such as Smurff or Tear Drop attacks are just some of the many methods to disrupt internal networking.
How easy is it for the average Joe to execute a DoS attack? There are tools available that can be used by a disgruntled employee to cause real havoc yet don’t require expert level knowledge. One example is Slowloris found at http://chers.org/slowloris. Slowloris is a low bandwitdth HTTP client used for issuing DoS attacks not using common flooding techniques. Slowloris holds connections open by sending partial HTTP requests to a target. The tool continues to send several hundred subsequent headers at regular intervals to keep sockets from closing overwhelming a target’s resources. This causes the target to be caught up with the existing request delaying responses to legitimate traffic.
Running slowloris is pretty simple. First download the .pl file and launch it using “perl slowloris.pl”. This will bring up the main screen. Next, run the command “perl slowloris.pl –dns YOURTARGET.com” to launch slowloris on a target. The next two screenshots shows slowloris running against a target I’ve blurred out.
Launching SlowLoris
Taking out a website (blurred) with SlowLotus
Another DoS tool is Low Hanging Ion Canon aka LOIC. LOIC was designed as a stress testing tool and can take out systems by sending a large sequence of UDP, TCP or HTTP requests to the target. Like SlowLoris, the attacker doesn’t have to understand how the tool works yet still be able to disrupt service by simply pointing LOIC at a target and launching the attack. To use this tool, you simply put in the target URL or IP and specify what and how often you want to send traffic.
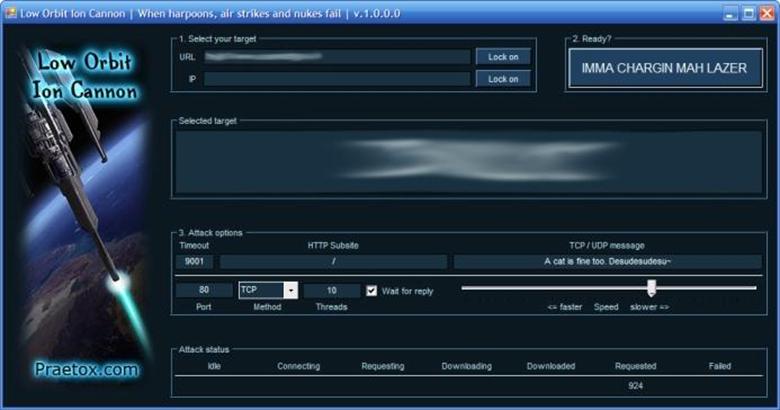 Main dashboard for Low Orbit Ion Cannon
Main dashboard for Low Orbit Ion Cannon
Defending against both Internal and External DoS attacks is slightly different. External defenses typically are tools placed between the ISP and your network gateway or capabilities enabled on your gateway equipment. Many firewalls have DoS detection and prevention settings. Some IT groups will place a IPS outside the external firewall as a means to detect and prevent DoS attacks understanding any other attack besides DoS is probably not a import item to be alerted to since its external to the network. There are a handful of vendors that provide more advanced external DoS prevention technology based on research from the leading ISP’s traffic, behavior triggers, etc. Examples include Arbor (covered HERE) and Radware. Radware is interesting since they recently announced a partnership at RSA 2014 to address DoS with Lancope, the leader for NetFlow and great Internal DoS solution. More on that announcement can be found HERE.
Internal DoS attacks are harder to detect since they can happen anywhere on your network. The most common techniques are reactive alerting tools such as Whats Up Gold that alerts when a system’s resources hits over 90% or goes down. Best practice for Internal DoS monitoring is viewing the entire network’s traffic and using analytics designed for detecting DoS threats rather than just waiting for systems to go down. The easiest way to accomplish this is through NetFlow since most network devices are capable of enabling NetFlow therefor becoming a detection point for DoS attacks. This includes sensitive traffic such as insider your Datacenter that typically is a blind spot for attacks yet critical for business operations. One NetFlow tool I always recommend is Lancope since it has both network performance as well as security analytical engines watching the traffic. This is key since many NetFlow systems collect flows but don’t know how to identify malicious traffic.
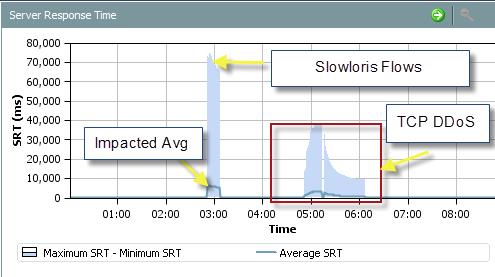
Lancope showing DoS attacks from SlowLoris and others
That last thing to consider on the defense side is enabling DoS features on your perimeter defense tools. If you are a Cisco customer, this white paper found HERE talks about some best practices and commands available that can be enabled for DoS detection and mitigation. I’m sure other Firewall, Content Filter, IPS, etc. tools have some form of DoS features that should be enabled if possible.
So to summarize defense, best practice is investing in a dedicated external and internal DoS focused tool as well as enabling DoS defenses on existing perimeter equipment. The low budget option would be dedicating a IPS to the outside however its probably wise to invest in a vendor that specializes in this attack. Internal defenses should use network trending, which the best method is through NetFlow. This way every network device is looking for DoS behavior (IE malformed packets, exploits, etc.) rather than purely waiting for devices to be taken out. Lastly, enabling DoS detection on your Firewalls, IPS, etc and prioritizing alerting will help reduce the risk. Alerting is key as downtime for many customers means lost revenue and negative impact to the company brand.