A Exploit kit is collection of redirection pages, landing pages, exploits and payloads designed to automatically infect users for a revenue stream. Exploit kits are typically not using targeted attacks meaning they try to get any system on the internet that is vulnerable to access their website and usually deliver ransomware. Examples of exploit kits are Kaixin / Gongda, Neutrino, Nuclear, RIG and Angler. Looking at Angler, it can exploit 9,000 systems on any given day and successfully compromise 5,400 of those systems. In terms of dollars, this can mean around $30 million dollars per year from the delivered ransomware. This post will cover whats involved with exploit kits including what can be done to protect your system from being exploited.
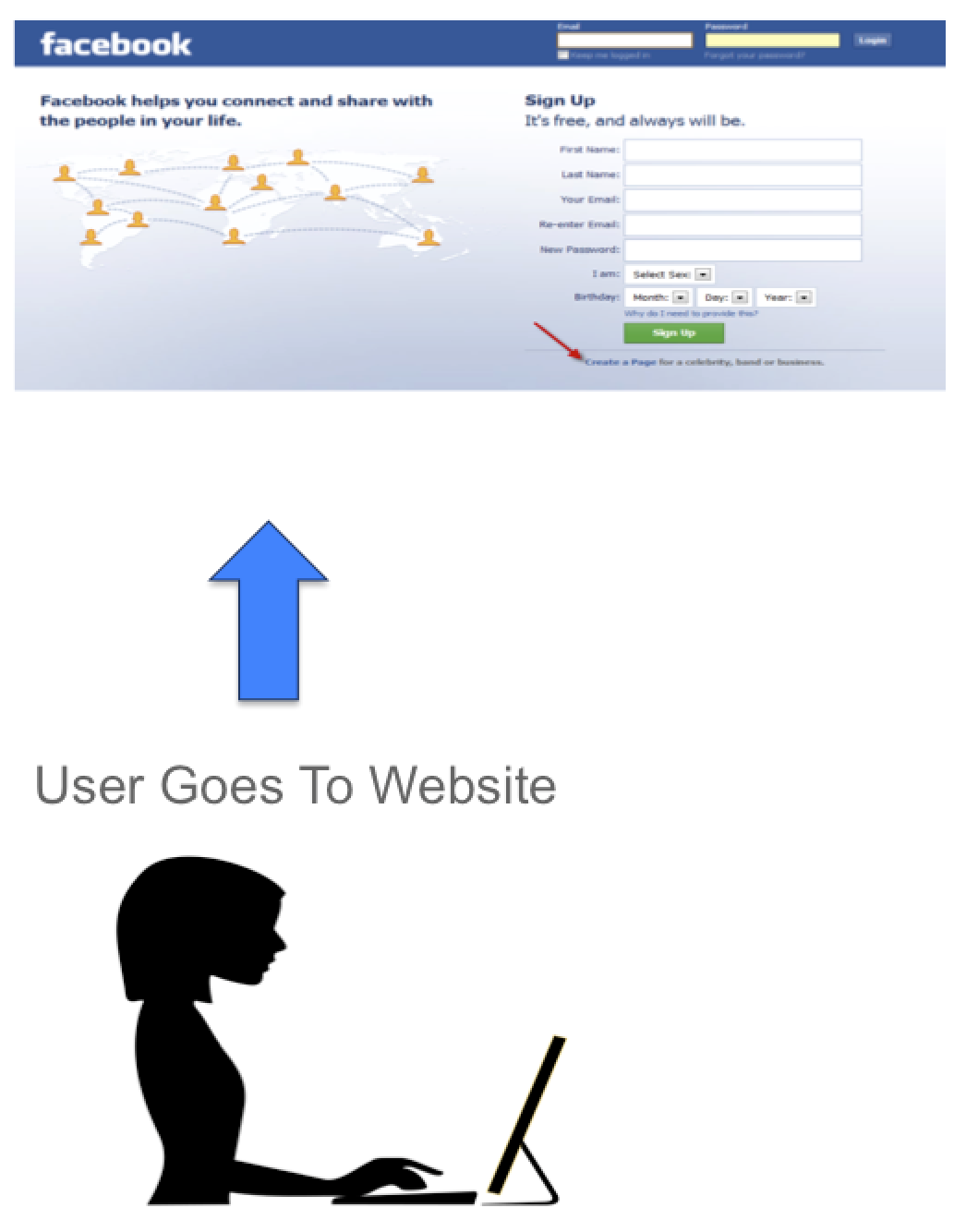
Lets start off by breaking down the components of a Exploit kit. The first part of the attack is getting clients to visit a website with malicious code, which we will cover later. A common method to get the client system redirected to the malicious website is through a compromised advertisements within other websites (also known as malvertising). For example, you may be on a social media website and stumble on a small advertisement page. It is important to understand that websites are like paint by numbers in that all the other pages happening within a website are also websites you are visiting. So an advertisement within Facebook would also be a website you are currently visiting, which could be how the attacker gets you redirected to their malicious website.
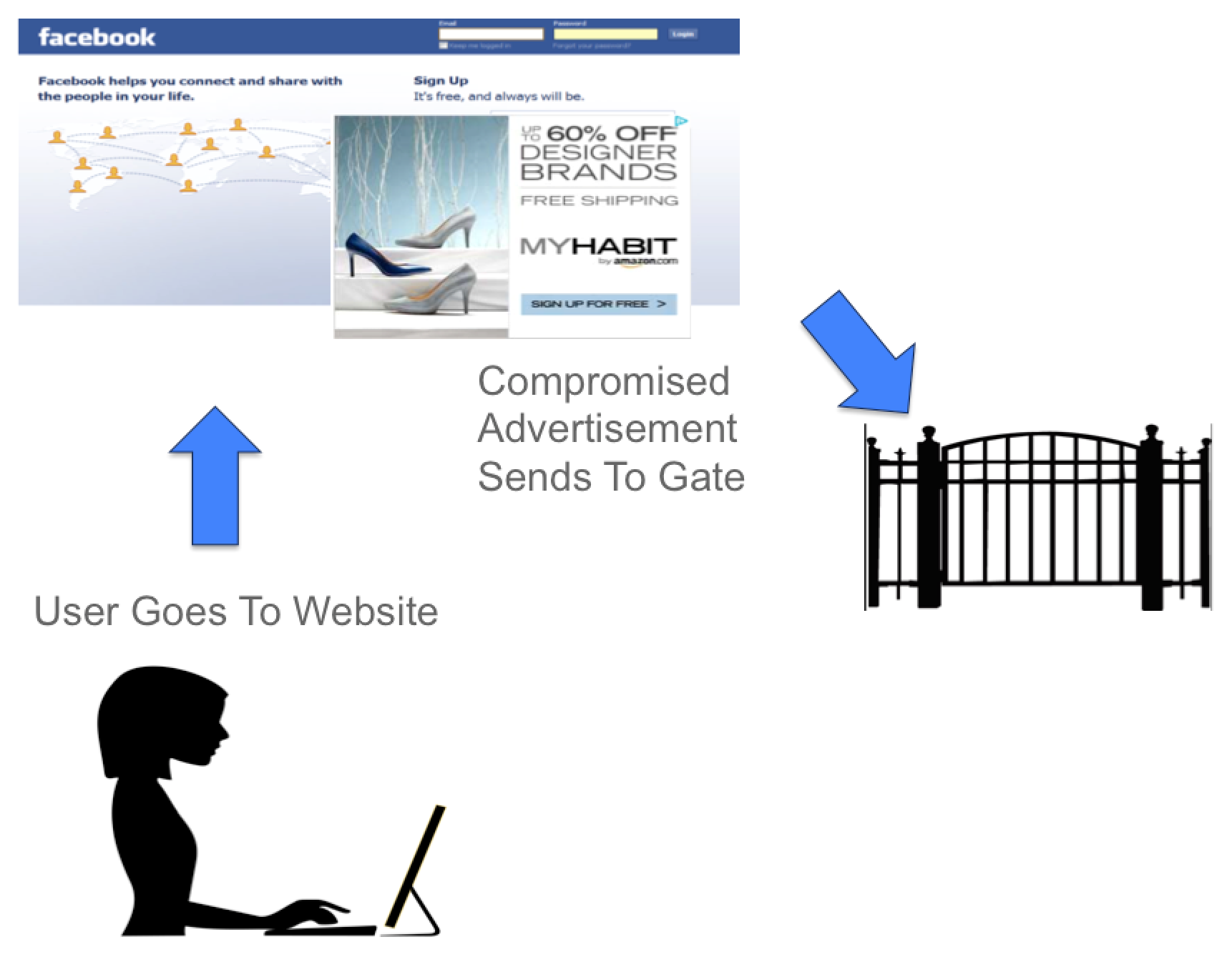 Step 2: Compromised Advertisement Sends User To Gate
Step 2: Compromised Advertisement Sends User To Gate
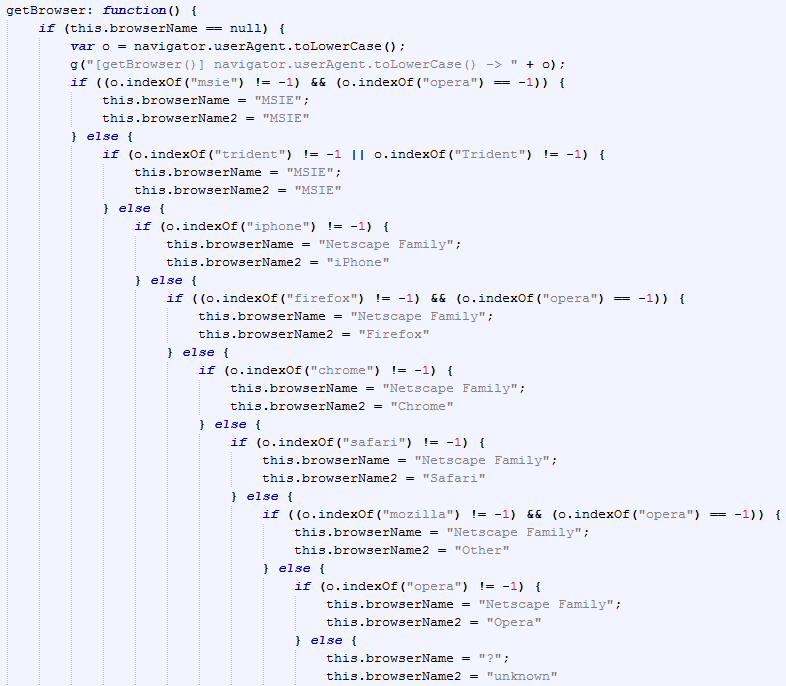
The attackers know there are people looking to identify them to prevent these types of attacks from doing harm to victims, so they typically have Gates put in place. The purpose of the gate is to evaluate the victim to see if they are a real system. They avoid security technology like Sandboxes as well as unique system that wouldn’t be able to be compromised by the Exploit Kit being used. Examples of systems Gates would avoid are honeypots and a web browser running uncommon software such as iceweasel. The next image shows gate code checking to see the browser type used by the victim (look at the if statement to see which version is being checked).
 If a victim is seen as being something that shouldn’t hit the landing page, the Gate will do something different meaning not send them to the landing page or send the user to another site to avoid exposing the real attack. Gates will change as they see how defenders are preventing them. It is common for this cat and mouse game to happen between the attackers and security researchers.
If a victim is seen as being something that shouldn’t hit the landing page, the Gate will do something different meaning not send them to the landing page or send the user to another site to avoid exposing the real attack. Gates will change as they see how defenders are preventing them. It is common for this cat and mouse game to happen between the attackers and security researchers.
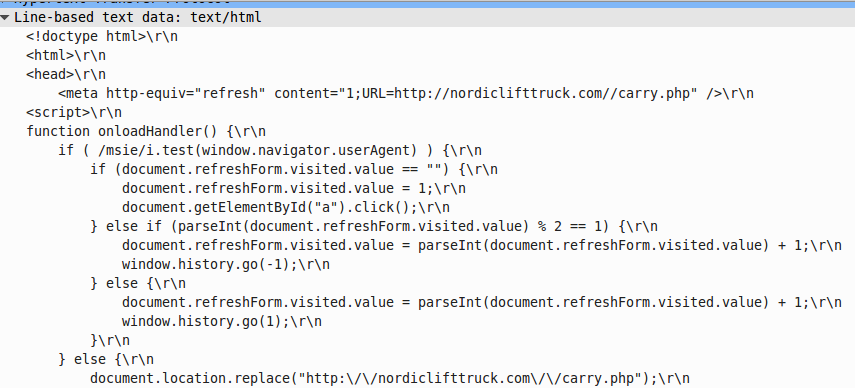 Angler Checking Browser History To Detect Sandboxes
Angler Checking Browser History To Detect Sandboxes
 Step 3: Granting Access To The Landing Page
Step 3: Granting Access To The Landing Page
If the Gate believes the system is real and could be compromised, it will move the system to the Landing Page. Landing pages are usually zero by zero frames so you don’t see it. They pull random text from websites to attempt to look like legit websites to avoid being detected by security systems. Hidden within the land page random text is the exploit code.
 Step 4: Delivering The Exploit
Step 4: Delivering The Exploit
Landing Pages will evaluate the victim for vulnerabilities such as Flash or Java and deliver a specific attack based on what vulnerabilities are matched. The exploit is usually something that isn’t a day zero meaning the vulnerability exploited usually has a known defense IE CVE associated with it. For example, Angler usually uses Silverlight (CVE 2016-0034) (learn more about this exploit HERE) while Kaixin will use Internet Explorer CVE 2014-6332.
 Step 5: Delivering The Malicious Code
Step 5: Delivering The Malicious Code
Many things could be delivered through an exploit launched by a exploit kit however with exploit kits, its usually something targeting a generic audience such as Ransomware. In the case of ransomware, the malicious code will attempt to phone back to a remote server from the victim’s system and perform a key exchange so the victim’s files can be encrypted and held for ransom.
Defending Against Exploit Kits
The most important thing to understand that there is a chain of events happening, which each step can be a place to detect and prevent the compromise. The industry calls this the kill chain. Your goal as a defender is to stop the attack as early as possible in the kill chain and do that for all attack vectors (LAN, Wireless, etc.). Looking back at this attack, the first part of the attack is the source delivering the attack. Reputation security (learn more HERE) can be your first line of defense for dropping malvertising within other websites so you never get redirected to the Gate. Many content filters offer general filtering however the good ones also have a security research team providing a reputation feed for these types of attacks. Cisco Talos is constantly scraping intelligence feeds for sites which match known malicious URI patters and blacklisting known gates.
The next stage is identifying something is trying to exploit you. Having your system up to date on patches is a great idea since many exploit kits leverage vulnerabilities that have patches available. It is also important to have anti-virus and Intrusion Prevention put in place to identify when a external system is scanning your system and attempting to exploit a weakness. This can be a combination of host and network security. These detection tools usually can be used at a few parts of the kill chain meaning they could detect when a landing page is trying to exploit you as well as the victim’s system phoning back to start the encryption process if ransomware is involved. There are a few Snort rules available such as these
Snort SIDs: 28613-28616, 29066, 29411-29414, 30852, 31046, 31130-31332, 31370, 31371, 31694, 31695, 31898-31901, 32390, 32399, 33182-33187, 33271-33274, 33286, 33292, 33663, 34348, 34720, 34969, 34970, 35109, 35110, 35256, 35333-35335, 35550, 36071, 36218, 36315, 36332
It is critical to also have breach detection technology to validate how effective your other security technologies are operating and identify when they fail. Breach detection targets the malicious code being delivered such as cryptolocker ransomware. The goal would be to identify when the code starts acting out of what is considered normal behavior such as modifying the master boot record, deleting files and so on. The next example shows Cisco’s Advanced Malware Protection technology informing an administrator that a file was quarantined based a few factors that prove its bad.
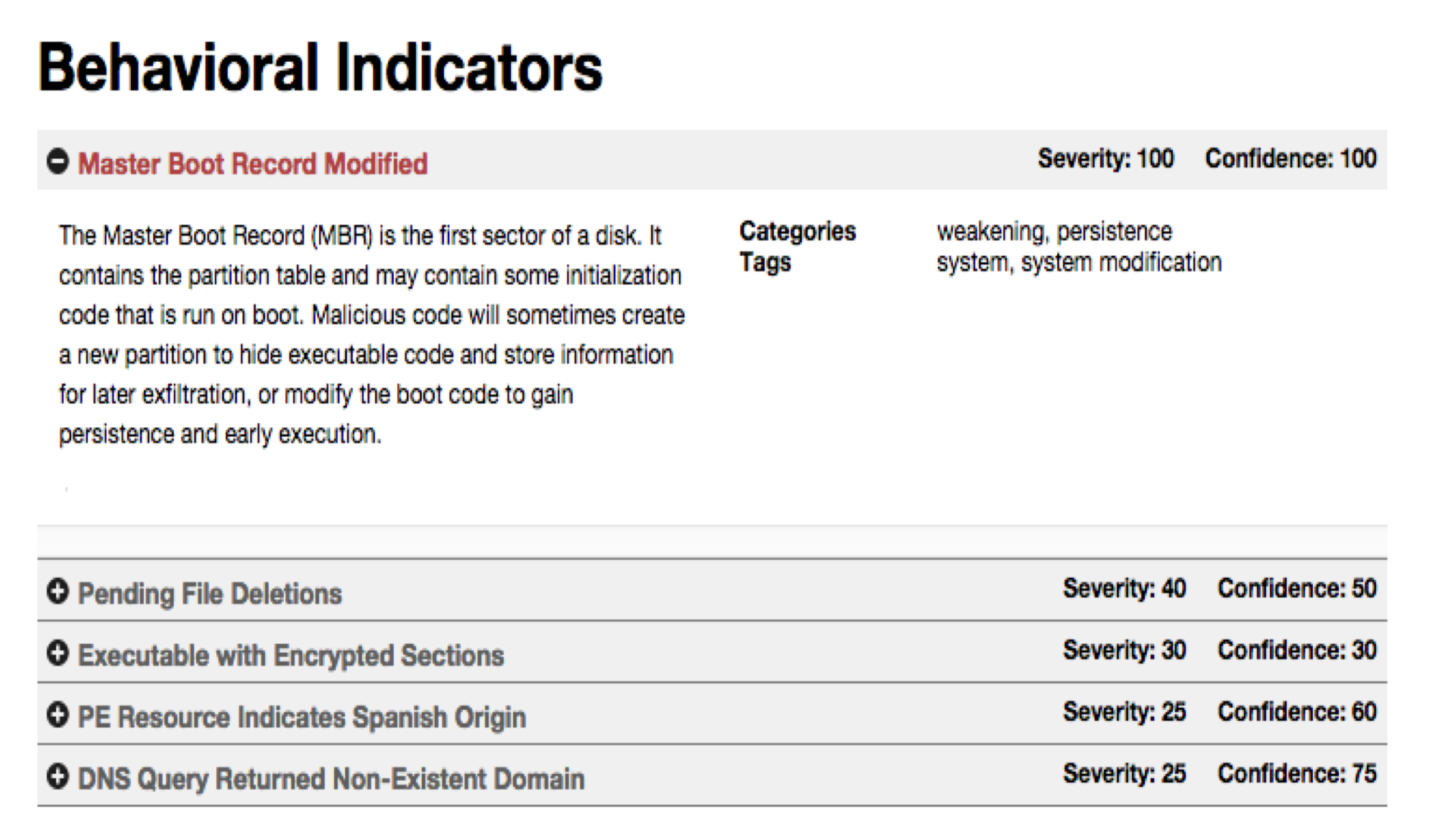 If you look at the previous screenshot, you may wonder what malicious software would act like this. Cisco AMP also lets you run a sample in a virtual environment and see what happens. In this case, its crypolocker as shown from running the virtual environment video.
If you look at the previous screenshot, you may wonder what malicious software would act like this. Cisco AMP also lets you run a sample in a virtual environment and see what happens. In this case, its crypolocker as shown from running the virtual environment video.
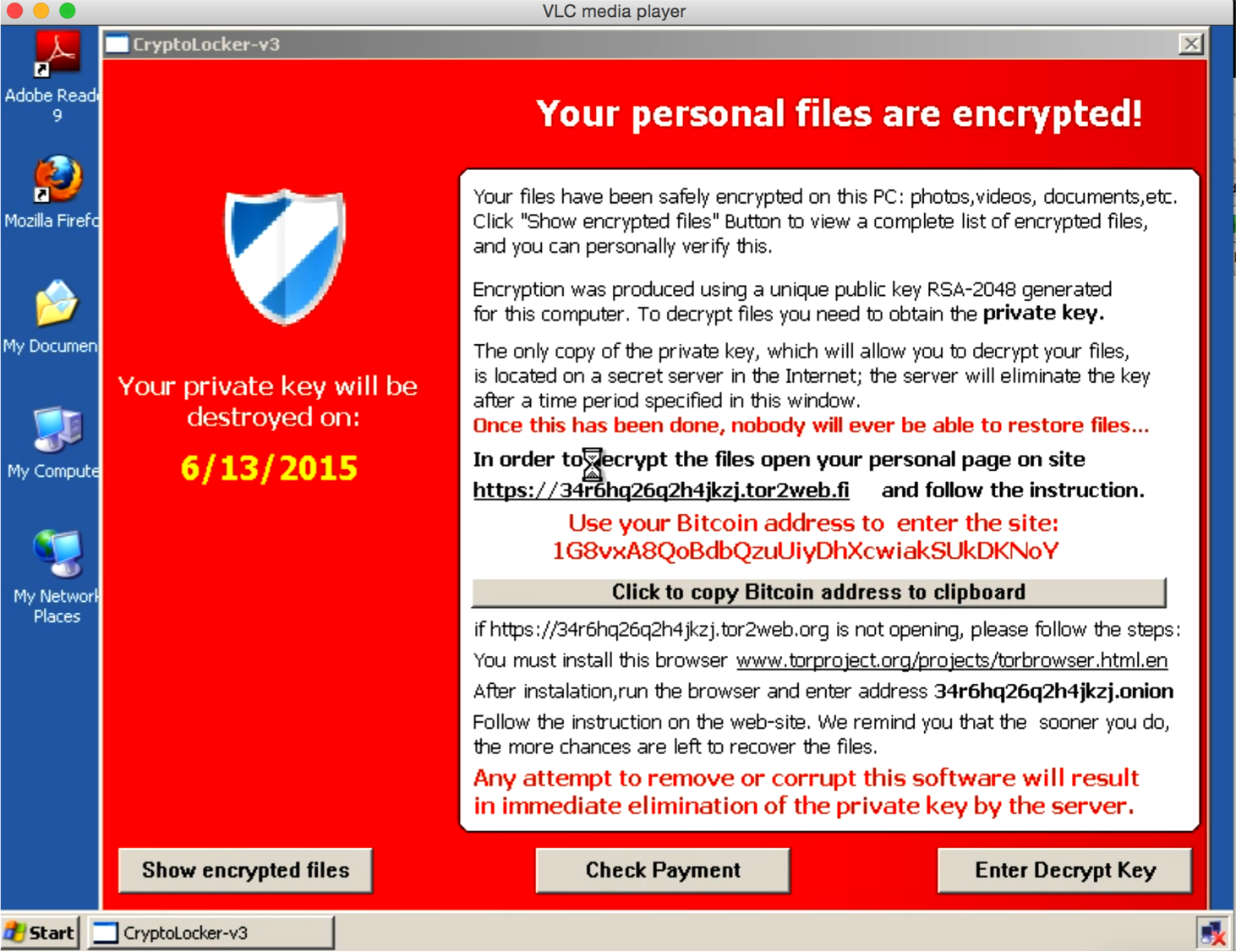 This seems very effective however it is important to understand this is just one attack vector. The previous example could be the Angler exploit kit, since Angler is known to deliver ransomware through malvertising. Another example of a exploit kit attack that is slightly different is the Locky ransomware typically delivered through email. In the case of Locky, you still would look at the kill chain by starting with the reputation of the source sending the email and next look at your anti-virus and other detection capabilities to determine if your email has something that will deliver malicious code (note this is probably not your edge unified threat management tool … its your email security solution). Breach detection would be used to evaluate files delivered through email with the hopes of determining they are not what they appear to be and stop the ransomeware from phoning out and encrypting the victim’s files.
This seems very effective however it is important to understand this is just one attack vector. The previous example could be the Angler exploit kit, since Angler is known to deliver ransomware through malvertising. Another example of a exploit kit attack that is slightly different is the Locky ransomware typically delivered through email. In the case of Locky, you still would look at the kill chain by starting with the reputation of the source sending the email and next look at your anti-virus and other detection capabilities to determine if your email has something that will deliver malicious code (note this is probably not your edge unified threat management tool … its your email security solution). Breach detection would be used to evaluate files delivered through email with the hopes of determining they are not what they appear to be and stop the ransomeware from phoning out and encrypting the victim’s files.
Hopefully this exploit kit 101 post helps explain how these attacks work. One last important concept is the idea of having visibility and data sharing across all of your security defenses to avoid security complexity. If each defense is not sharing data, you will have a tough time completely removing a compromise. Lets say one of your users has a breach detection technology flag they are infected at the host level. You should be able to identify the infection and see who else has that same file across your network. You should be able to go back in time and identify who was the first person to get infected IE patient zero. You should be able to investigate patient zero to understand HOW THEY ARE VULNERABLE and WHAT SOURCE ATTACKED THEM. If you can’t do this, most likely you will only kill part of the compromise and get breached the same way through another victim.