One common question I’ve been asked is what are the current requirements to perform authentication, authorization, and remediation when using VPN (usually Cisco ASA VPN) and Cisco Identity Services Engine ISE. This post will cover this subject however I suggest for those with Cisco ASA 9.2.1 and ISE should reference this really good configuration guide found HERE.
Cisco ISE is a solution that tells you who and what is accessing your network for LAN, VPN and Wireless, controls what type of access is provisioned (VLANs, ACLs, dACLs, SGTs, Guest Access, etc) and enforces policies regarding what state the device should be in (IE updates, anti virus, etc) before permitting network access. Many administrators are extremely concerned when providing remote devices access to the internal network since its possible that networks outside of their control are more vulnerable to attack. Also, remote users may use their systems for non-business activities that increase the risk for host based compromises. These threats could pass through the remote connect and impact the internal network.
Combining ISE with VPN solves this problem by verifying the user and system is approved, checking the posture or “health” of the system and provisioning proper access upon connecting to the network. VPN keeps traffic behind the protected “corporate barrier”, which typically has more advanced security defenses than the average home network (IE high end IPS, Content Filtering, etc). This also prevents network based attacks such as “man-in-the-middle attacks” since traffic is encrypted between the host and corporate network.
ISE uses 802.1x, MAC address based checks (MAB) and Redirection to enforce authentication and authorization of systems. This can be done the same way for LAN, VPN and Wireless meaning ISE doesn’t require any additional hardware for any of these access methods. One situation that requires an additional piece of ISE hardware known as a Inline Posture Node (IPN) is when providing remediation for VPN aka enforcing posture on endpoints coming over a VPN connection. NOTE: This doesn’t apply for VPN when remediation is not a requirement. The reason why is VPN concentrations can’t perform Change of Authorization aka CoA like supported wireless and switches meaning they can’t change the attributes of an authentication, authorization, and accounting session after a user or device has been authenticated. The IPN acts like a bump in the wire between the VPN concentration and network providing CoA for incoming VPN connections.
NOTE: A ISE IPN must be a physical appliance meaning you can’t virtualize a IPN like other ISE appliances.
The recent release of ASA 9.2.1 code changes this concept since with this release, RADIUS CoA is supported. This means you no longer need a Inline Posture Node (IPN) to perform remediation for VPN users like supported switches and wireless access points. After a VPN user logs in, ASAs with 9.2.1 or later can redirect traffic to ISE so ISE can provision a NAC or Web Agent. From there, the standard posture process is performed with results being sent back to ISE. If the machine is deemed compliant, ISE will send a RADIUS CoA. This diagram shows the traffic flow.
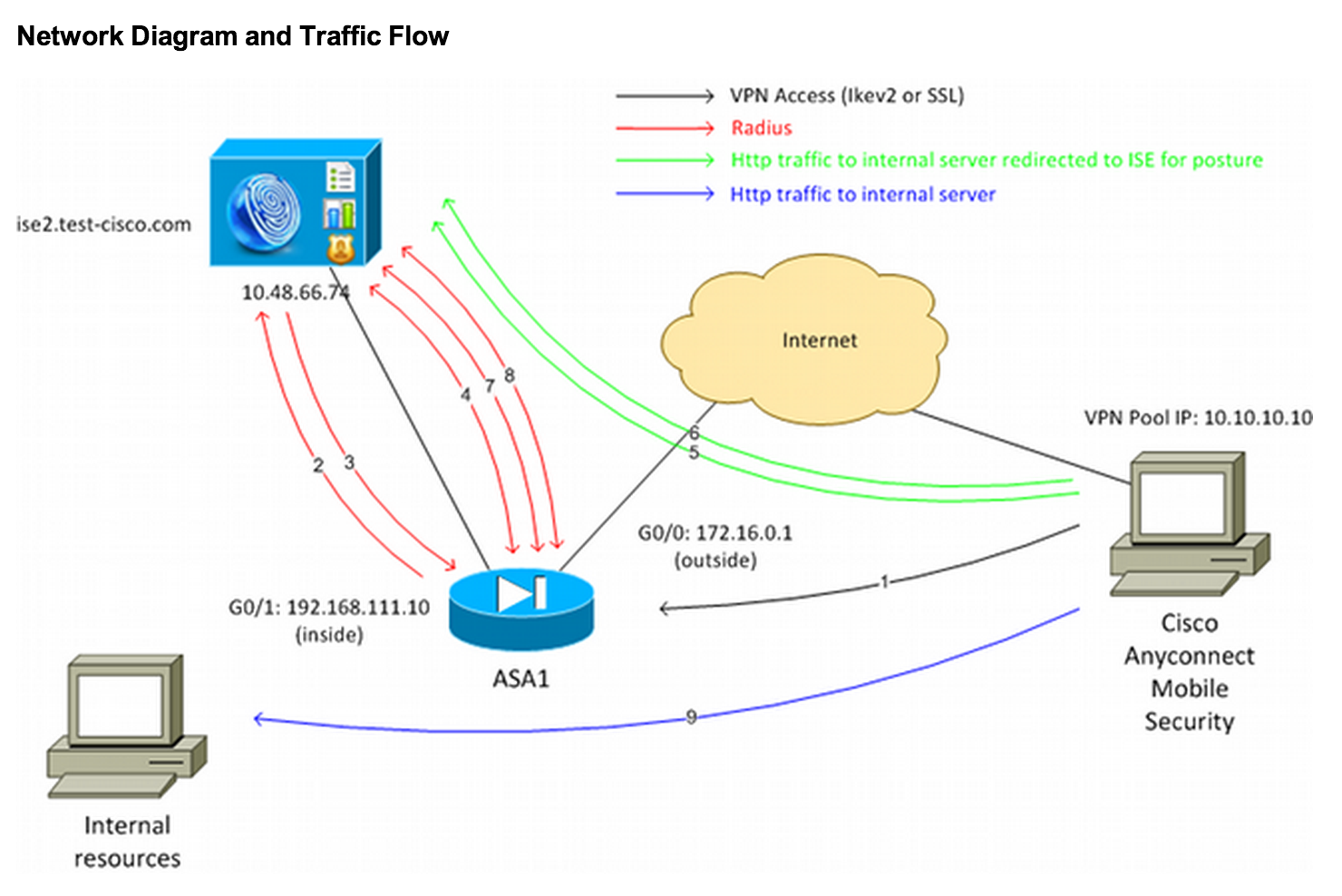
The results of the posture validation are then sent to the ISE. If the machine is deemed complaint, ISE can send a RADIUS CoA to the ASA with the new set of authorization policies. After successful posture validation and CoA, the user is allowed access to the internal resources based on policies set by the ISE administration.
NOTE: This requires at least ISE 1.2 and ASA 9.2.1. For all other VPN concentrators or older version of ASA code, a IPN is required for VPN remediation using ISE as of the time of this writing. Once again, this configuration guide walks through the process to set this up found HERE. For non ASA or pre ASA 9.21 VPN concentrators, check out the standard IPN configuration guide for that setup found HERE.




