There has been some recent chatter about the recently seen Shamoon attacks. Cisco’s research team Talos posted about this HERE providing a good overview of what is involved. They also included the associated snort and Clam AV signatures. Here is that article.
Shamoon is a type of destructive malware that has been previously associated with attacks against the Saudi Arabian energy sector we’ve been tracking since 2012. We’ve observed that a variant of Shamoon, identified as Shamoon 2, has recently been used against several compromised organizations and institutions. Talos is aware of the recent increase in Shamoon 2 activity and has responded to ensure our customers are protected. Additionally, Talos will continue to monitor for new developments to ensure our customers remain protected.
PROPAGATION
Shamoon 2 has been observed targeting very specific organizations and propagating within a network via network enumeration and the use of stolen credentials. Some of the credentials are organization specific from individuals or shared accounts. Other credentials are the default accounts of products used by the targeted customers.
COVERAGE
Coverage for Shamoon 2 is available through Cisco security products, services, and open source technologies. Note that as this threat evolves, new coverage may be developed and existing coverage adapted or modified. As a result, this post should not be considered authoritative. For the most current information, please refer to your Firepower Management Center or Snort.org.
Snort Rules
- 23893
- 23903
- 23905-23933
- 24127
- 40906
ClamAV Signatures
- Win.Dropper.DistTrack-*
- Win.Trojan.DistTrack.*
- Win.Malware.DistTrack.*
AMP Detection
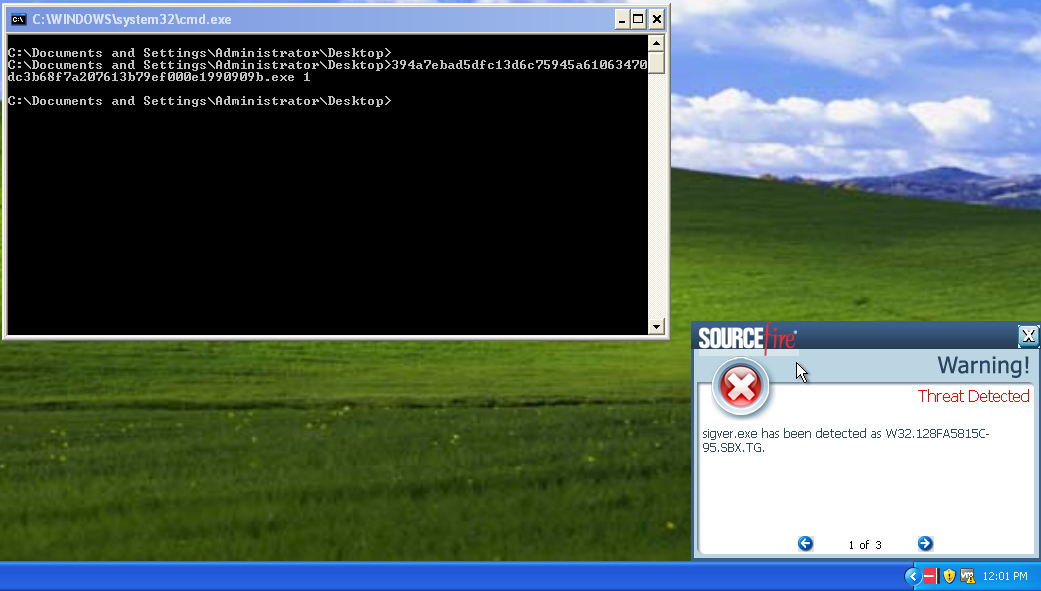
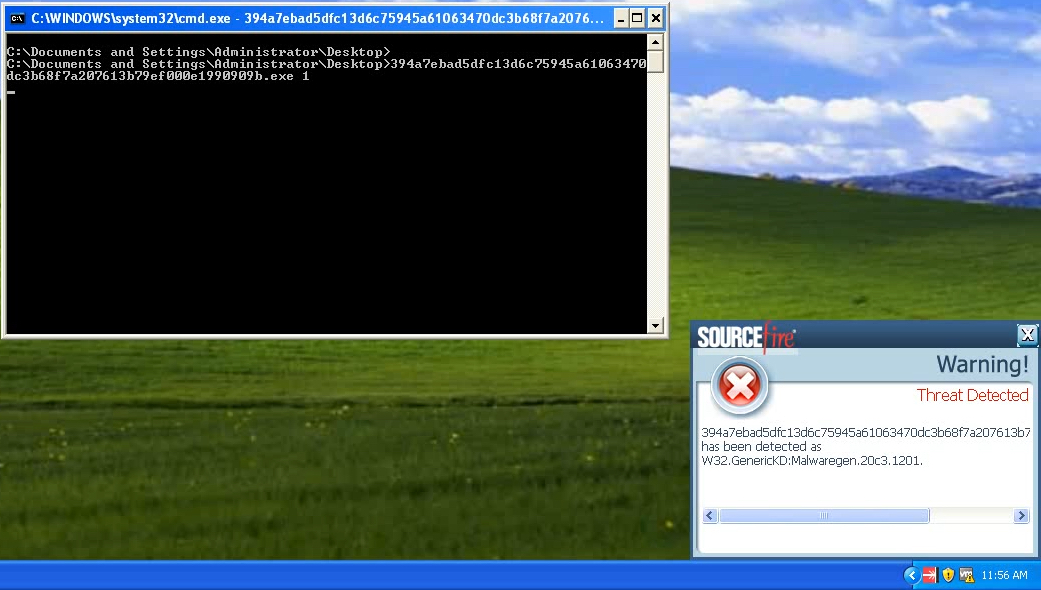
- W32.GenericKD:Malwaregen.20c3.1201
- W32.Malwaregen.19nb.1201
- W32.47BB36CD28-95.SBX.TG
- W32.Malwaregen.19nb.1201
- W32.Generic:Malwaregen.20c3.1201
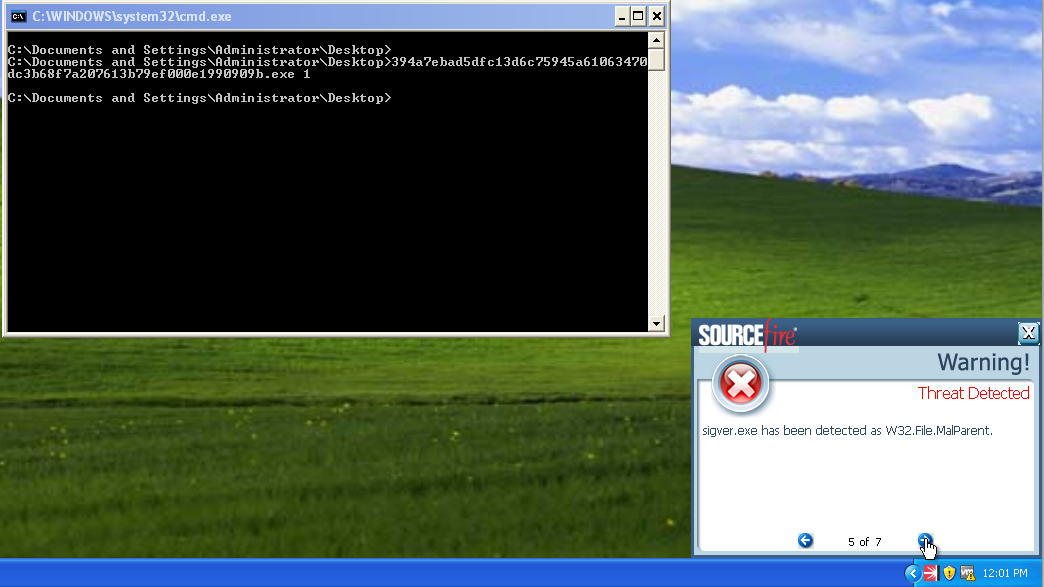
- Win.Malware.DistTrack
- W32.128FA5815C-95.SBX.TG
- W32.C7FC1F9C2B-95.SBX.TG
- W32.EFD2F4C3FE-95.SBX.TG
- W32.010D4517C8-95.SBX.TG
- Win.Malware.DistTrack.Talos
Other Mitigation Strategies
Recent Shamoon 2 activity serves as a good reminder that users and organizations need to have a comprehensive disaster recovery plan. No one can say for certain if you will be targeted by destructive malware but we can say with 100% certainty that all drives fail. Without a proper system to backup and restore your data, you risk permanently losing your data. Ensuring your assets are properly backed up and can be quickly restored is critical should a system become compromised by Shamoon, ransomware, or other destructive malware and require a complete restoration.
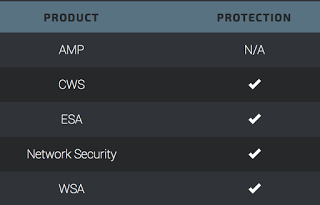 Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware used by these threat actors.
CWS or WSA web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
The Network Security protection of IPS andNGFW have up-to-date signatures to detect malicious network activity by threat actors.
AMP Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.