In a previous lesson, I pointed out that there are three essential ways security tools detect threats. Those methods are signature-based, behavior, and anomaly detection. Most security tools use a combination of one or more of these capabilities to detect threats. The following figure represents this concept.
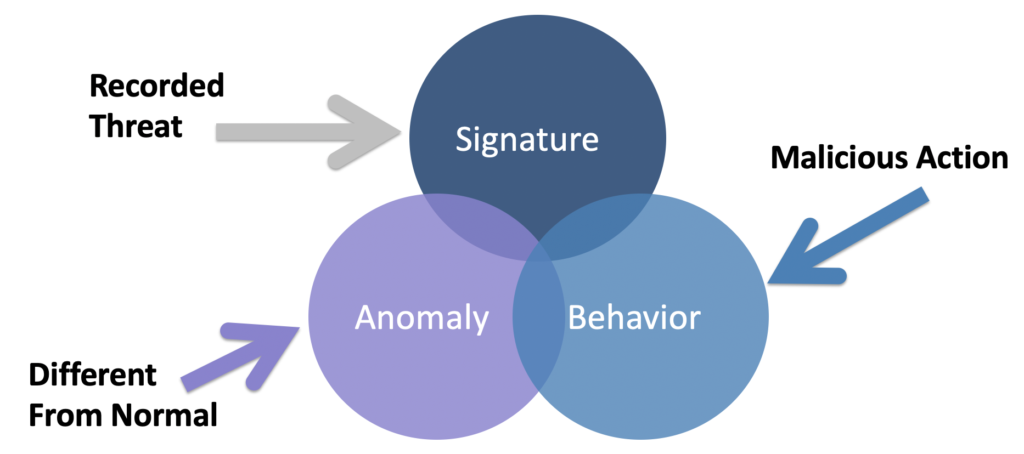
Signature detection requires knowing what to look for and comparing hashes or other strings to identify a match. Signature detection is a common feature found within antivirus and IPS/IDS products. Behavior detection looks for malicious or other known behavior characteristics and alarms the SOC when a match is made. An example is identifying port scanning or a file attempting to encrypt your hard drive, which is an indication of ransomware behavior. Antimalware and sandboxes are examples of tools that heavily leverage behavior detection capabilities.
The third capability is what I’ll focus on in this post, which is to look for anomalies. I believe this capability is the future of security and I see this is where a lot of the current innovation is occurring in the security space. It takes into consideration hot topics including big data, threat intelligence, and “zero-day” detection. I believe everybody needs to be aware of how this approach to security to better understand the future of the security market space.
Identifying Normal
Before you can determine something is an anomaly, you must first understand what is considered normal. This makes up the first part of any anomaly detection capability which is understanding normal behavior. Establishing normal can occur in two ways. One way is to learn an environment over a period of time and map out common behavior known as baselining the environment. The other approach is to pull in a ton of historic data and immediately compare things against it to find outliers. First, let’s look closer at the first approach, which is baselining.
Baselining
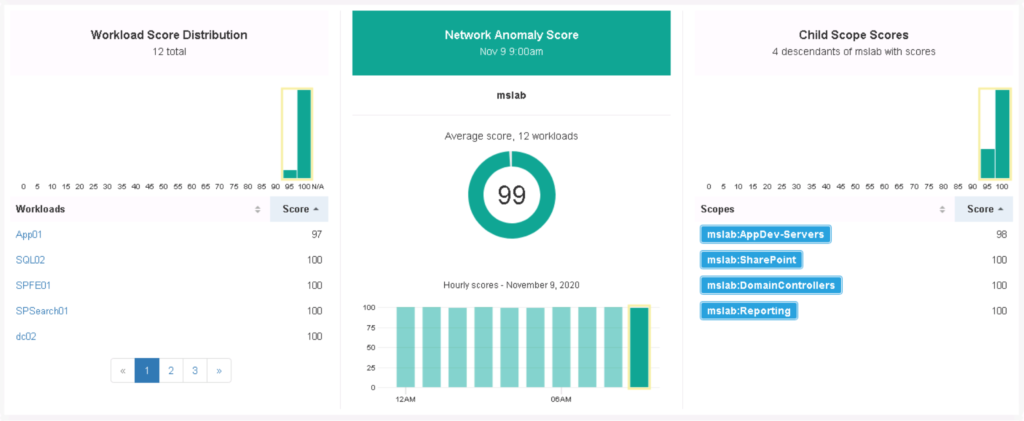
Learning about an environment means collecting data. Many bleeding-edge host security tools are designed to monitor any process running on a host and map out its behavior. As this occurs, if any unusual activities are seen, an anomaly can be detected and investigated. Cisco Tetration is an example of this type of technology, which allows the creation of allow lists (also referred to in the industry as whitelisting). The concept works by not only mapping normal behavior but also learning relationships between applications. Learning everything about a host includes monitoring all processes running as well as how they communicate with other processes. Over a period of time, one process talking to different processes can also be part of the baseline if this activity is considered normal behavior. This larger baseline concept leads to the ability to dynamically learn and adjust an allow list without human interaction since changes are considered normal, hence the technology can permit the traffic based not just on a permit list but permit behavior that has been established within the baseline. The next image shows an example of Cisco Tetration baselining workload distribution behavior, network traffic behavior via how applications are communicating with the network, and child activity also known as processes that are being run.
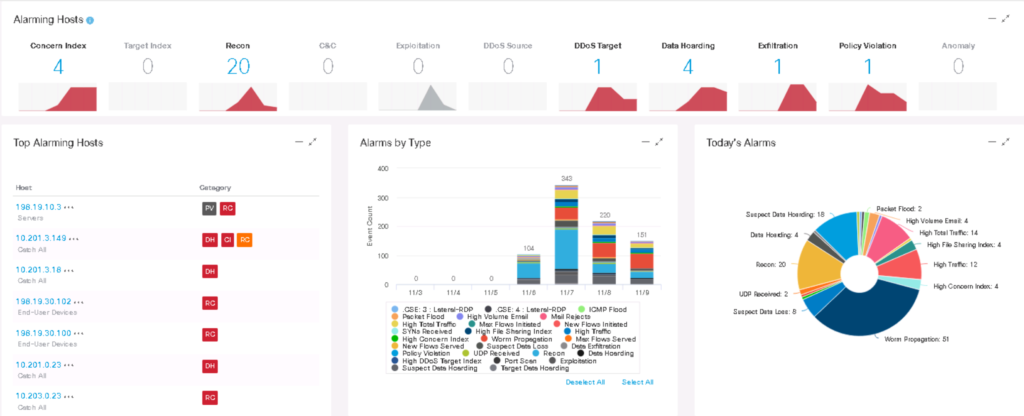
There are network tools that can also function in a similar manner. Cisco Stealthwatch and Plixer are two examples of tools that learn network behavior through baselining and identify when unusual behavior is seen. In both the endpoint and network example, the longer the tools run, the more normal data is collected, and a better baseline is established. This means unlike other threat detection approaches, administrators do not need to spend countless hours adjusting the tools also called “tunning”. Anomaly tools actually get smarter over time on their own just by collecting data. The next image shows Cisco Stealtwatch using baselining to detect various types of network based threats.
Big Data Baselining
The second approach to understanding normal behavior leads us to the big data conversation. The previous baseline approach is good, but it is limited to what is normal within what the security tool can see. If other people’s baselines are added into the mix, you open up a much more powerful understanding of the concept of normal. For example, let’s say there is a new day zero that nobody has ever seen and it’s trying to install itself on your endpoint. Its activity should look different than the behavior of any application that has installed itself on your host. Now think about looking to see how similar applications have acted across thousands of systems around the world along with the baseline of what you know as normal. If the day zero claims to be a upgrade.exe file for a Microsoft product, threat intelligence based on big data can take that file and see how it compares to other upgrade.exe file activity as a similar file is installed on thousands of systems around the world. If 99.99999% of the time the file acts one way and you find your version is acting different, a big data baseline will immediately point out your version of upgrade.exe is not normal.
Anomaly Detection’s Future
I believe the future of security detection will be heavily leveraging anomaly detection capabilities. Storage and compute are continuously increasing allowing for easy learning and storage of how things work both from a network and process viewpoint. By taking that data from your systems, taking data from hundreds of thousands of similar systems, and looking for what is not normal, one can detect almost anything unusual allowing for a very strong security detection tool. Threats would have to not only operate without detection using stealth techniques, but they would have to look normal compared against the average device’s behavior.
Today, malware developers test exploitation against systems within their lab before going live however, this big data anomaly concept flips that approach upside down since the attacker’s lab will not look anything like real world system behavior. Malware development would need to change, which I predict future malware will include behavior learning techniques to keep up with how security is moving towards anomaly detection as a foundational approach to detecting threats. Cybersecurity is a cat and mouse game, which means it is constantly changing. Hopefully this post about the next big shift in cybersecurity capabilities is helpful for understanding a bleeding edge security technique that exists today and will continue to become better over the next few years.
Labs
You can go to dcloud.cisco.com and create a free account right now. There are Stealthwatch and Tetration labs you can look up to test out anomaly detection concepts. Anybody with a email can do this.