My buddy Aamir Lakahni at drchaos wrote a interesting post about criminals using RAT tools to steal boat loads of money from banks. The original post can be found HERE.
Another week, another hack. A group of cybercriminals used phishing attacks to install remote access toolkits (RATs) and steal over $300 million from banks and other financial institutions (source: http://www.nytimes.com/2015/02/15/world/bank-hackers-steal-millions-via-malware.html)
Using RATs is not new, and common method cybercriminals use. We had an in-depth look at njRAT and the Sweet Orange Exploit on this site. It is also not uncommon to use phishing and other social engineering attacks by attackers to trick users into installing sophisticated malicious tools.
According to the New York Times:
The bank’s internal computers, used by employees who process daily transfers and conduct bookkeeping, had been penetrated by malware that allowed cybercriminals to record their every move. The malicious software lurked for months, sending back video feeds and images that told a criminal group — including Russians, Chinese and Europeans — how the bank conducted its daily routines, according to the investigators.
Raising security awareness and education is going to be a key defense against these future attacks. Security professionals are already questioning why these banks would have such sensitive system on the Internet. Government and other agencies at least try to air gap their sensitive systems by sing separate networks with no, or extremely filtered and limited Internet access.
Early reports seem to indicate social engineering played a big role in obtaining sensitive information and allowing attackers to complete large transfers. Let’s not forget the critical and sensitive information that can be obtained with a pretty face and social engineering. If we need a reminder we just need to look at Emily Williams.
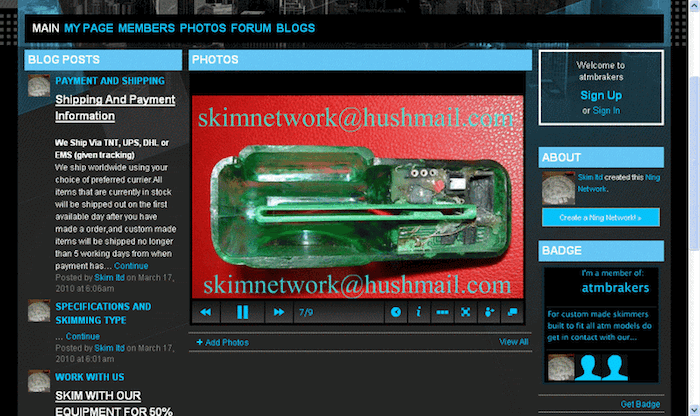
Malware is not the only thing consumers need to worry about. We browsed some common DarkNet websites and found sophisticated skimmers being sold for approx $1500 to $2000.
Services sell skimmers openly are always coming up and being shut down by authorities. They are constantly changing their web addresses or the more sophisticated sellers are selling them on Ghost Markets like the recently shut down SilkRoads or other .onion sites on the TOR Dark Web networks.
 Modern skimmers will record PINs and other codes and record them along with the credit card number.
Modern skimmers will record PINs and other codes and record them along with the credit card number.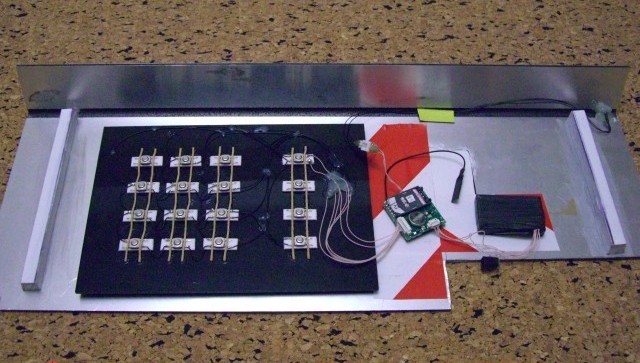 We uncovered complete DYI skimmers that were tested with popular credit card locations such as gas stations, ATM machines, and vending machines. These complete kits sell for $3500 or higher, but within a few hours attackers can be up and running and collecting credit card numbers for criminals.
We uncovered complete DYI skimmers that were tested with popular credit card locations such as gas stations, ATM machines, and vending machines. These complete kits sell for $3500 or higher, but within a few hours attackers can be up and running and collecting credit card numbers for criminals.