Cisco has been in the firewall business since the mid 90s. They have built upon that platform by adding VPN and now various “next generation” security features such as IPS/IDS, Reputation blocking and Application Visibility and Controls all from a single solution. This is know as ASA CX (more on ASA CX found HERE and how to build a lab found HERE). The latest release just came out June 30th and available for download. The ASA 9.3 release notes can be found HERE.
Here is an overview of whats new with 9.3
-
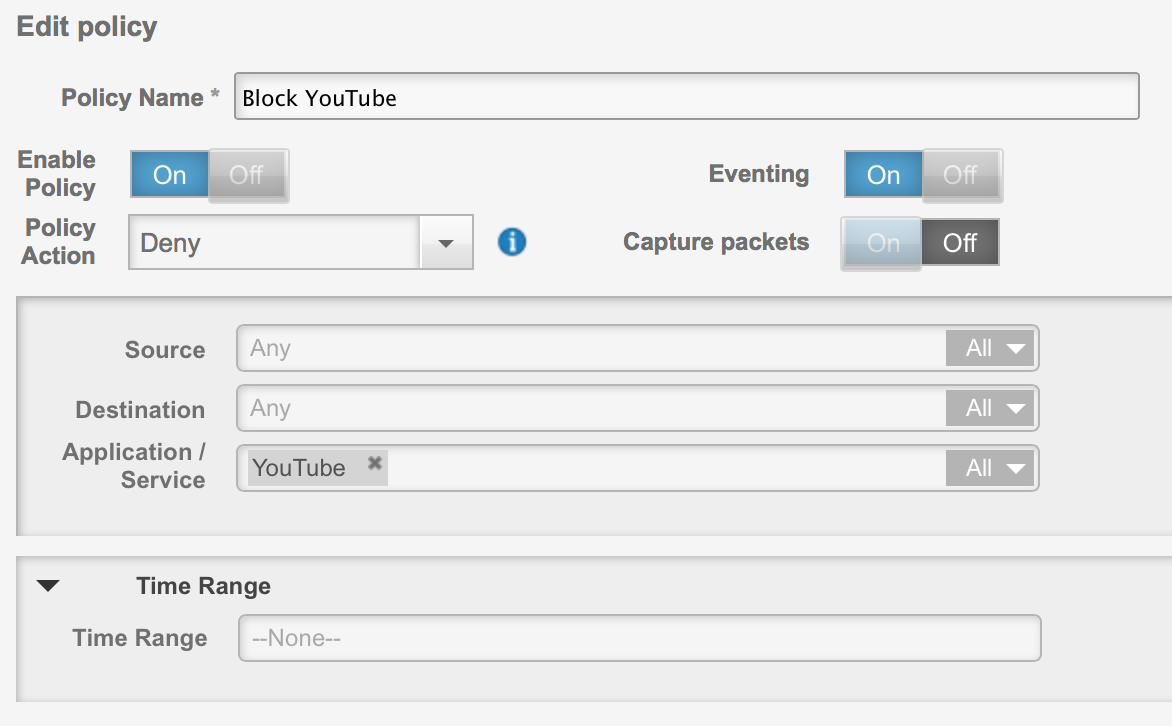
Time ranges for policies. For example, I have a deny youtube policy shown below. Now I can run it for a specific time range for time-sensitive access control
The list of well-known root Certificate Authority (CA) root certificates is now periodically updated through the same updater service that is used to download new signatures and other components.
Names in Components listed in updates are more meaningful
You can send events to syslog servers! 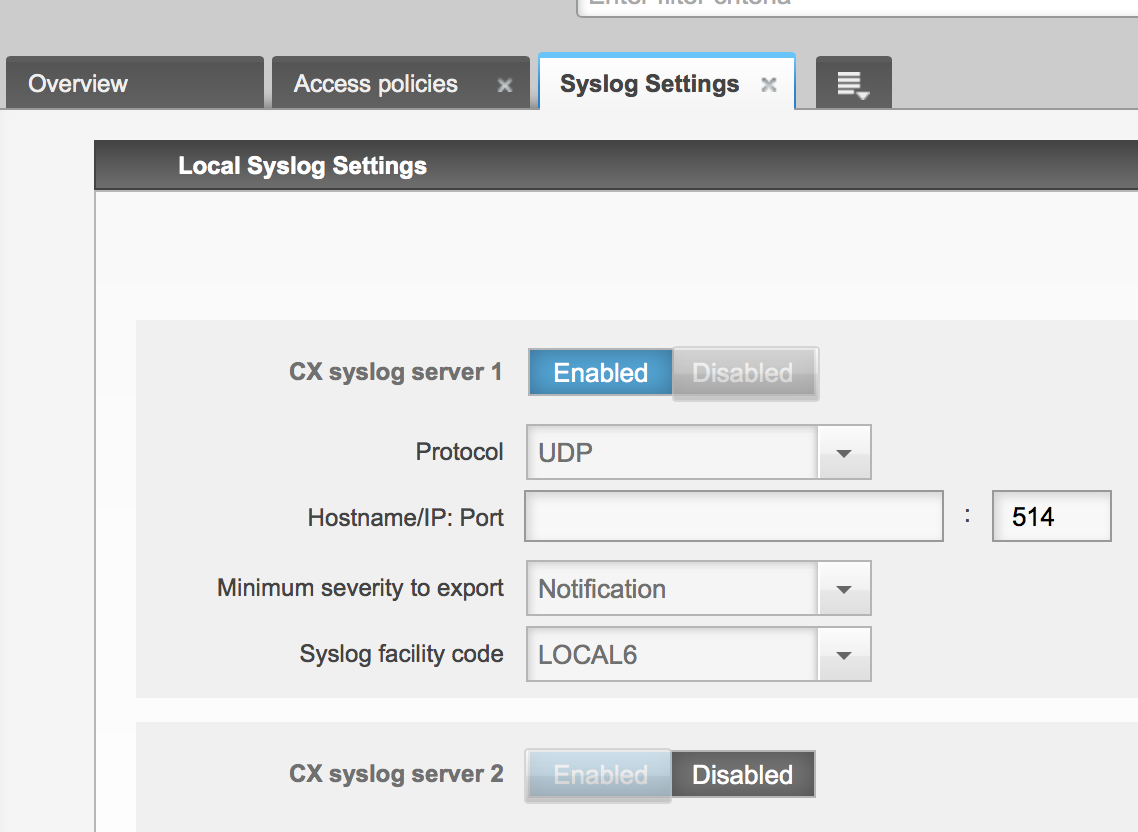
Create policies that match uncategorized applications or application types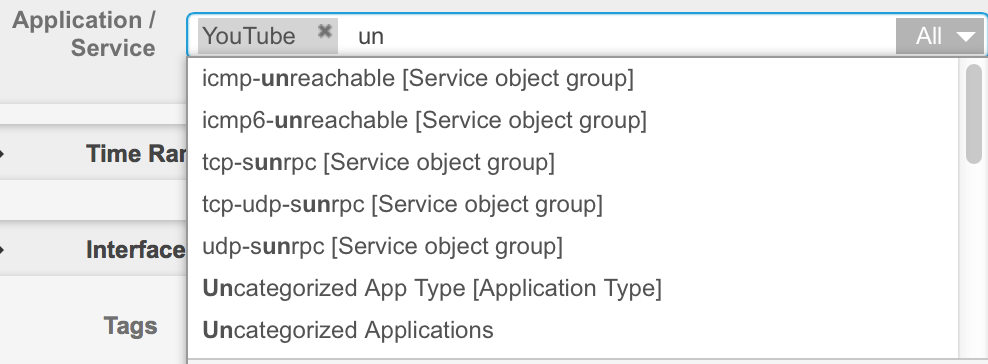
Create URL filtering policies for uncategorized URLs
You can now have more than one Active Directory realm per CX device, and import these realms into PRSM
They added a dedicated tab for web filtering categories (I really like this) 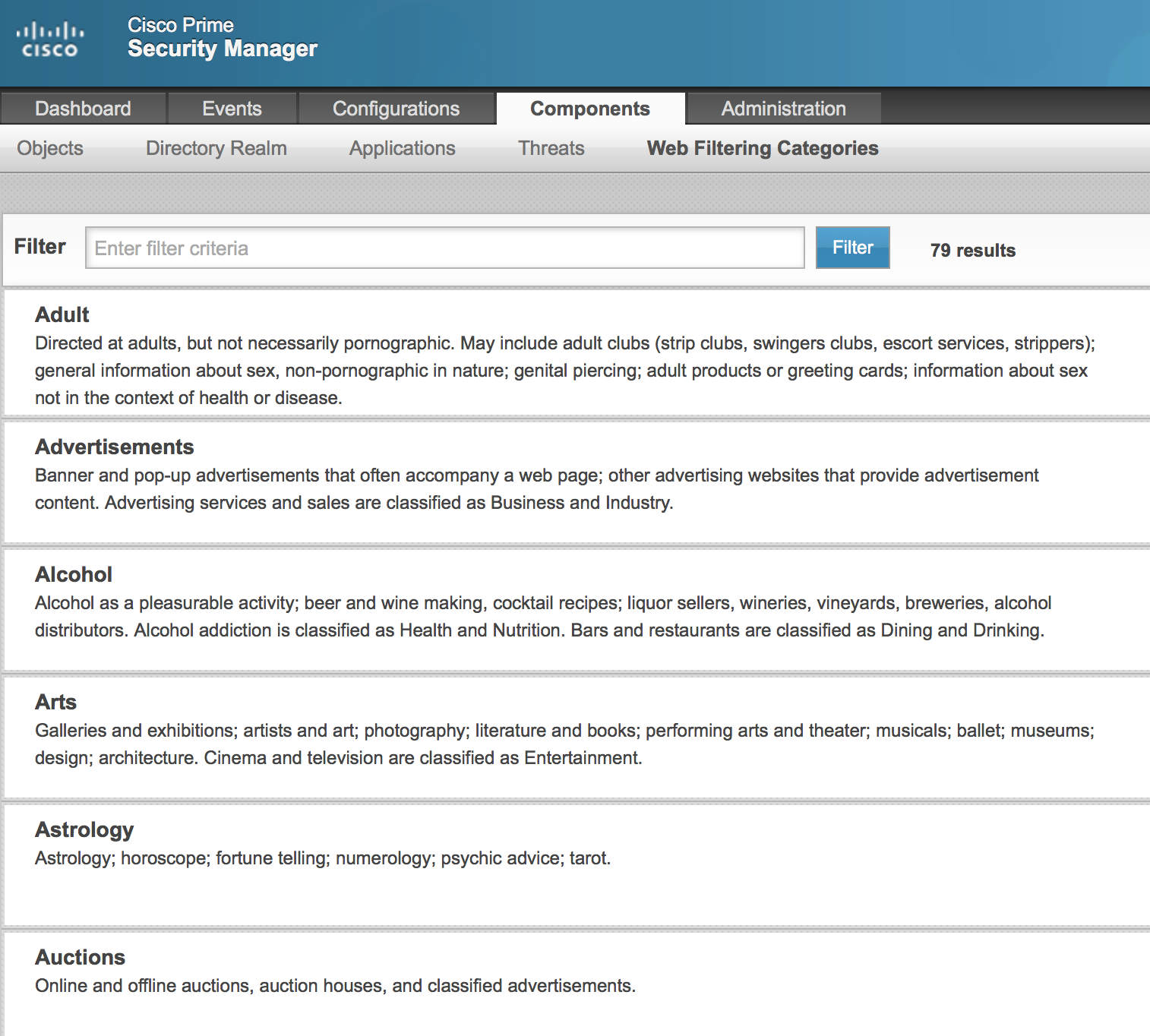
You can now create identity policies that prompt for active authentication using a browser form that you customize. Below is the default template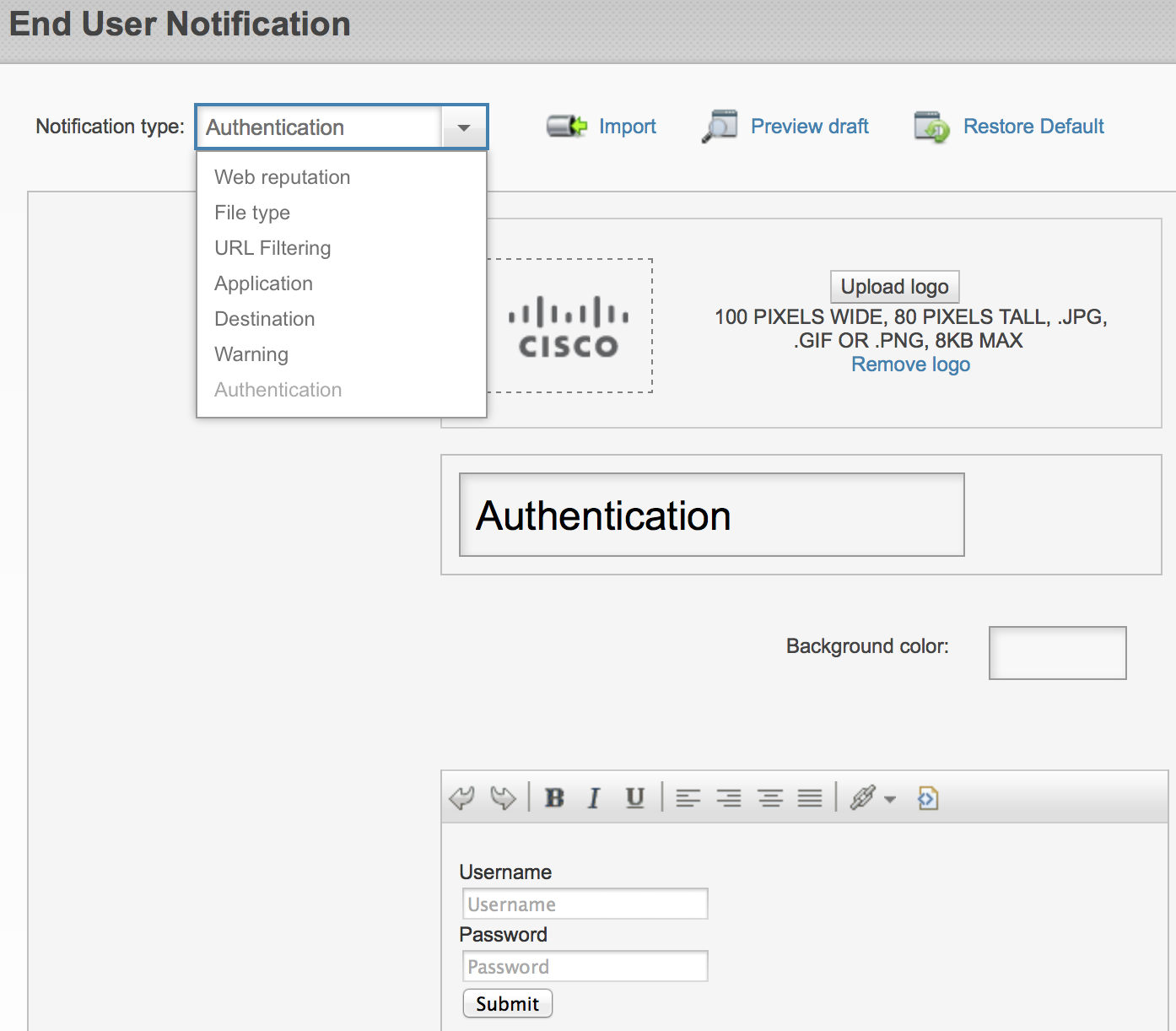
You can identify users who fail active authentication as guest users, and write access policies to provide special treatment for guest users.
You can now create application filtering policies based on cloud services tags. There is a new dashboard for monitoring cloud services applications shown below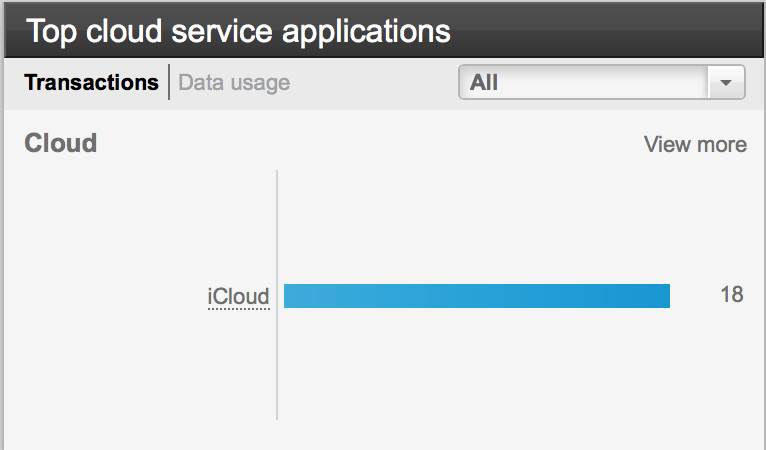
There is now a page that lists the web categories and their descriptions. From this page, you can also look up the category for a web site, or its reputation.
You can now configure a secondary Context Directory Agent (CDA) to provide a high-availability setup
Support for YouTube for Schools. You can create an access policy that inserts your school or district ID into the appropriate HTTP Request header to limit YouTube access to educational videos.
The HTTP proxy now works for network participation in addition to component updates
Improvements for “do not decrypt” actions as well as the decryption engine now supports Elliptic Curve Cryptography (ECC) cipher suites
More CLI commands
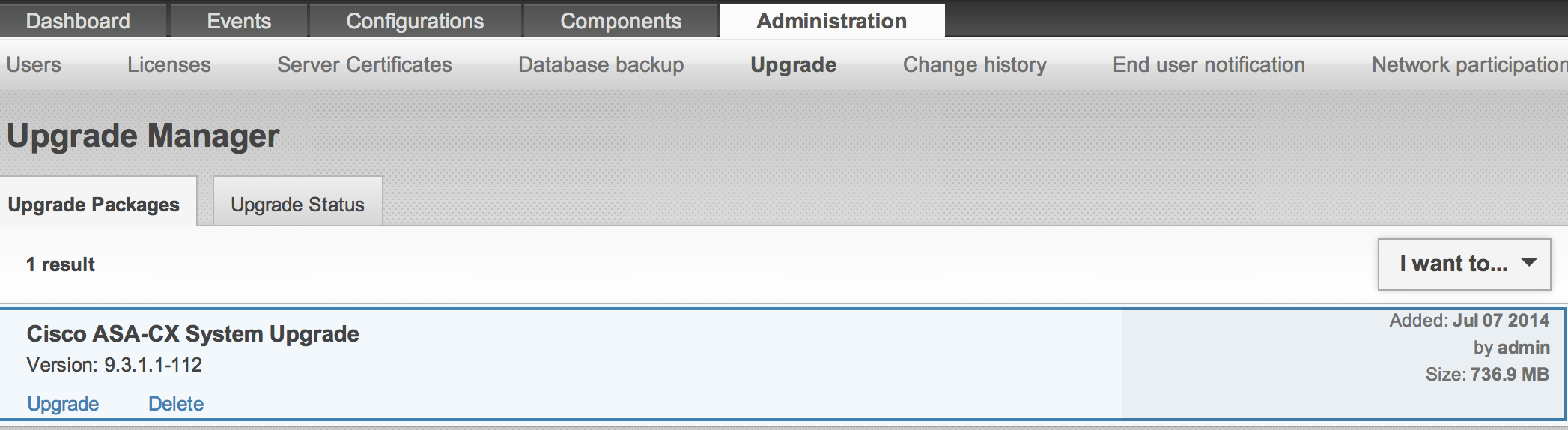
Upgrade Procedure
The first thing to do is download the asacx-sys-9.3.1.1-112.pkg file from Cisco.com. You will need a CCO account and smartnet contract. Once you have the file, log into the ASA CX GUI. Select Administration and Upgrade. Next select I want to and select to upload the .pkg file. Once uploaded, it will verify the file. This should take a few minutes to do. When its done verifying the file, you will see the option to upgrade.
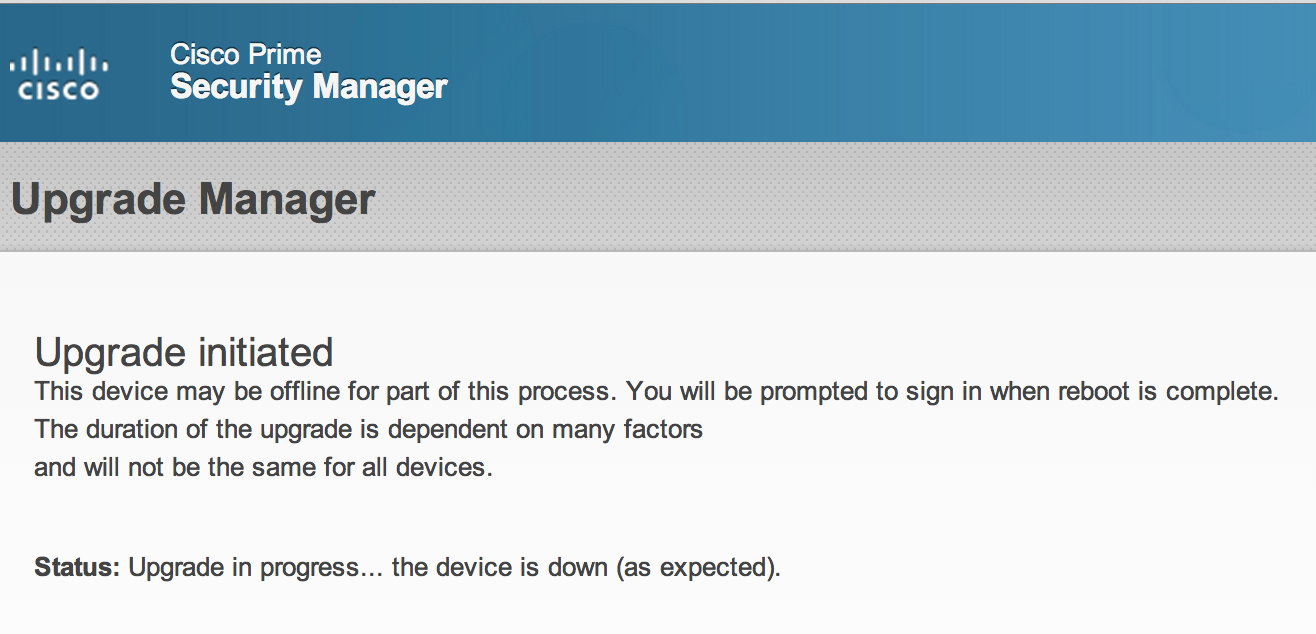
The upgrade process takes around 15-20 mins. The GUI will change to the image below and show the status as the system upgrades. Once complete, you will see a message to try logging in again to verify the upgrade worked properly. If you try to go to the GUI while its upgrading, it will show the GUI being down.
 BTW for those wondering about the ASA CX being vulnerable to Heartbleed, here is a note from the release notes covering this
BTW for those wondering about the ASA CX being vulnerable to Heartbleed, here is a note from the release notes covering this
“Heartbleed Bug
The Heartbleed bug (CVE-2014-0160) is an OpenSSL vulnerability that uses invalid TLS heartbeats to gain inappropriate access to data on a device. ASA CX 9.3.x and PRSM 9.3.x are not vulnerable to the heartbleed bug. However, CX devices do not prevent invalid heartbeats from passing through the device as traffic between other endpoints. Ensure that you patch your vulnerable endpoints with the required fixes.
You can learn more about this bug at heartbleed.com or other resources on the Internet.”