Cisco acquired the leader for identifying day zero threats ThreatGRID around may of 2014. ThreatGRID’s statement “The First Unified Malware Analysis and Threat Intelligence Solution” sounds like a mouthful however represents its purpose of going beyond what most “sandbox” technologies accomplish in this market space. What is also interesting is this technology is being moved into other Cisco security offerings now that they are part of Cisco’s breach detection strategy.
The first thought many people have when hearing “malware analytics” is sandboxing threats. ThreatGRID does leverage sandboxing however that’s a small part of the value seen from this solution. The real value is the threat intelligence meaning the data achieved from TheatGRID’s team analyzing around 300,000 samples a day. What this means is you get the bigger picture of what a threat is and you get that information really fast. On average, analyzing one or many samples takes around 7.5 minutes. The output report can tell you how the malware works, where it intends to communicate with, what will be downloaded or modified, other known associated malware with a threat and so on.
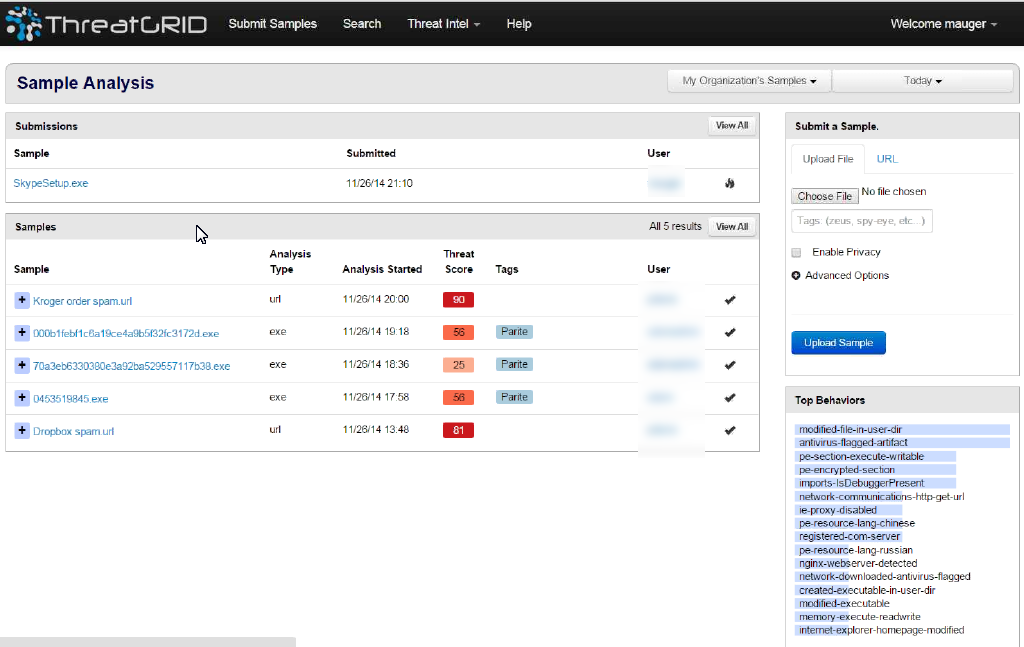
Lets take a look at the ThreatGRID dashboard.
Here is the main dashboard. The first thing to notice is the list of samples, their threat score and users that submitted them (blurred out in this example). Users can submit a sample using the Submit Samples tab and selecting a file or specifying a URL. Samples can be anything such as a .exe, .dll, .jar, pdf, .rtf, .doc, .ppt, zip, .sep, URLs, etc.
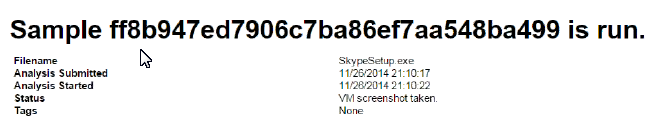
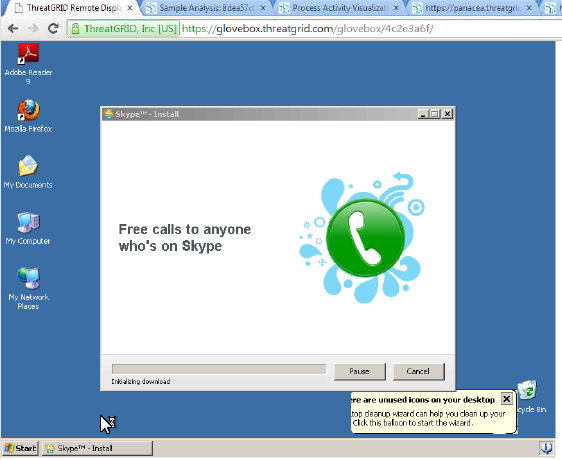
Samples are given a hash and ran in a environment you can modify such as rebooting, installing things, etc. while the sample is being analyzed. The next two images show a sample hash and a sandbox analyzing a sample while the admin runs skype as well as other programs.
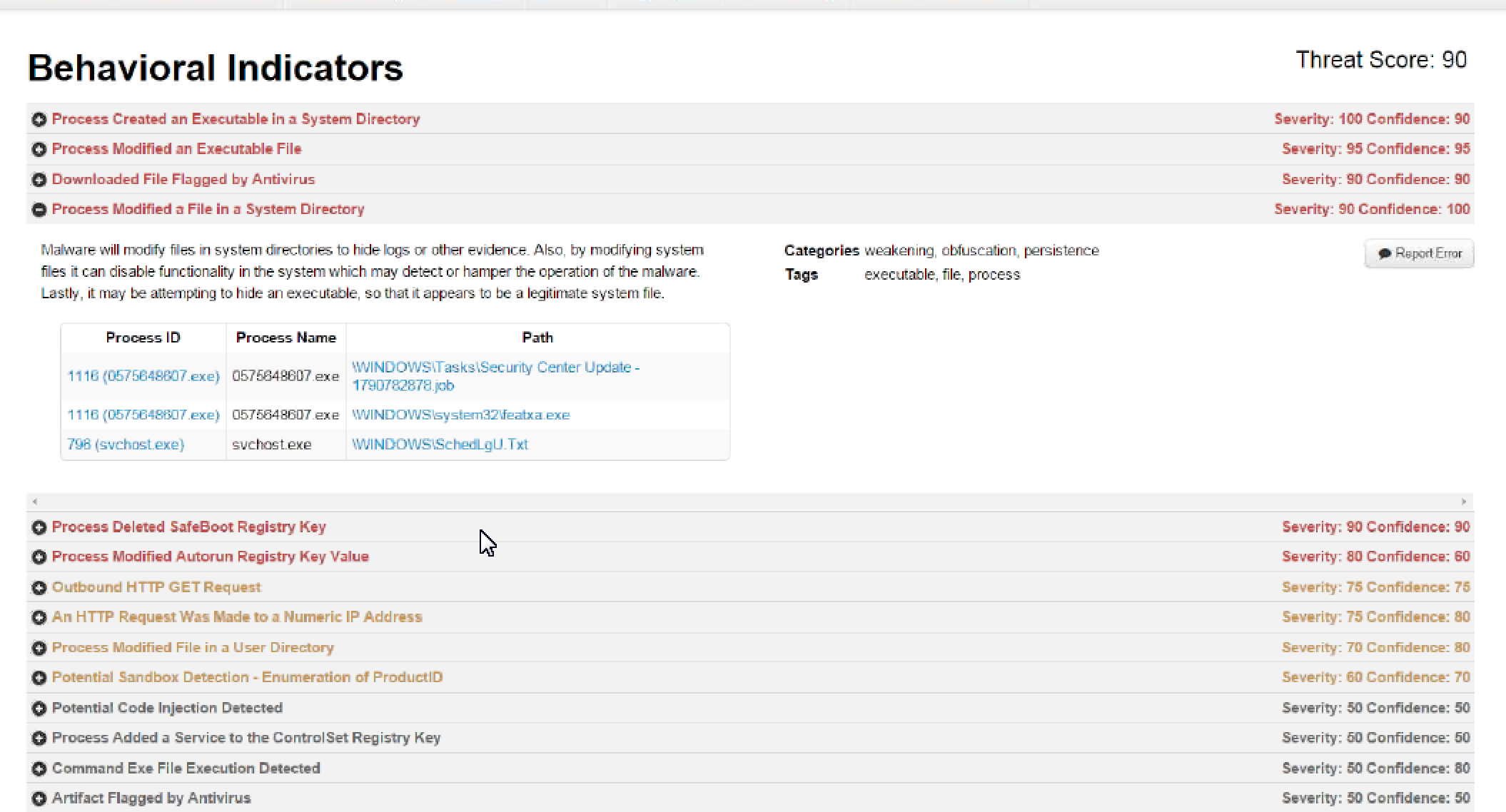
Once the sampled is played for a few minutes (depending on how this is customized), ThreatGRID terrors it down and shares the report across a global database. The output report provides data such as what was modified as well as how it related to things like domains, other file hashes, etc. The key feature to the analytics is it is outside of the sandbox meaning there isn’t triggers malware writers can identify to write around. The next screenshot shows an example report explaining how this malware sample modified 3 system directory files. Administrators can know exactly what was changed so they can implement the appropriate remediation to all infected systems.
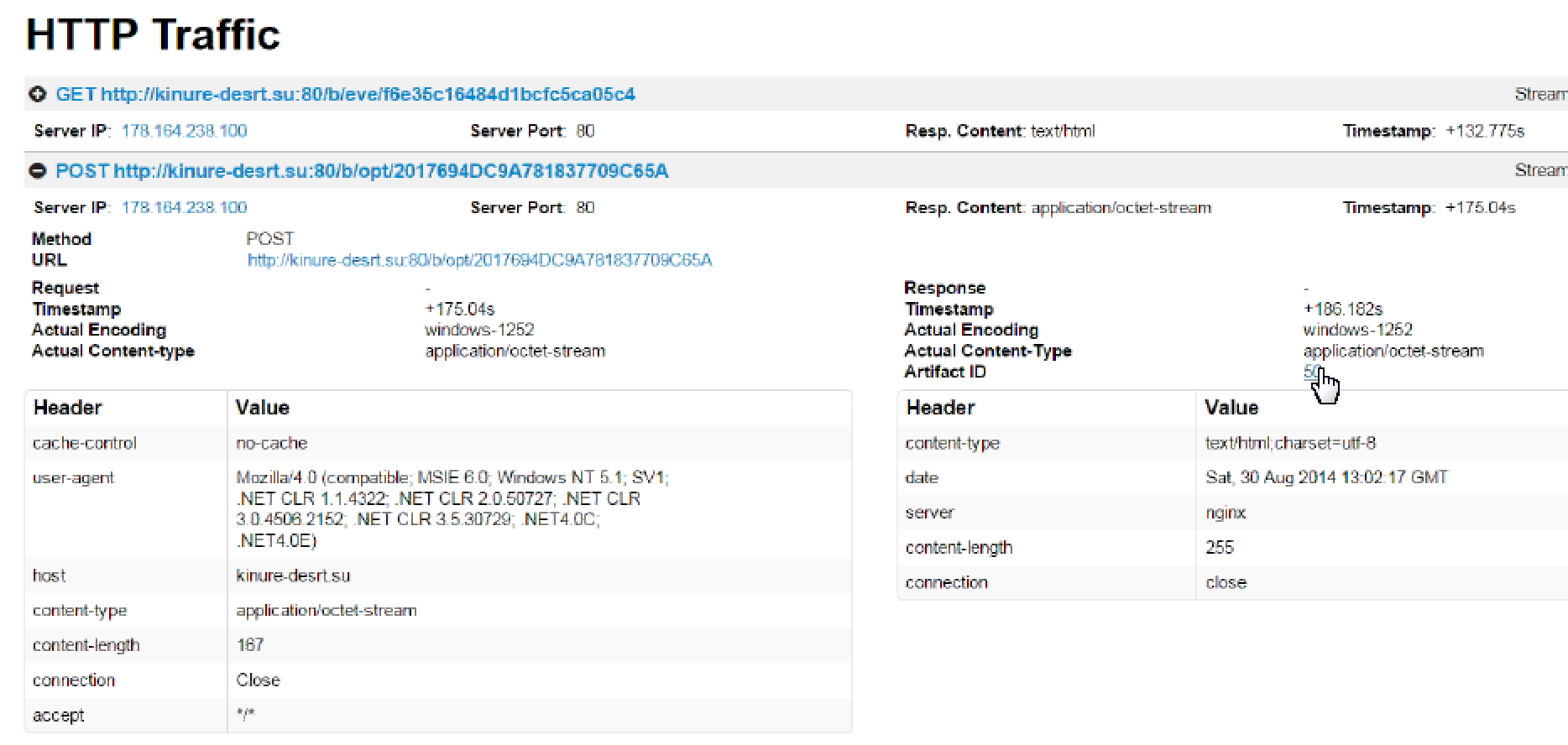
Here is an example of identifying get and post commands trigged by malware sample.
Today ThreatGRID comes as a cloud or appliance offering. Appliances can keep samples local or share them with the global database. The future is adding ThreatGRID into other Cisco products as well as being the guts of other Cisco threat detection capabilities.
This post just scratches the surface of the power of the data seen by ThreatGRID. There are many other features and use cases such as tools to break down how a malware is coded, leveraging the built in API to enhance other tools and so on. If you are looking for a tool to give you full visibility of possible malware for your security operations center, this is the only tool that can provide this much detail, fidelity, speed and sample size on the market. Learn more at http://www.threatgrid.com/