The future of security must reach beyond the capability of an appliance. There are too many attack vectors that are continuously changing to detect with a silo solution. It basically comes down to this …. there are only so many signatures that can be checked against as well as behavior algorithms that can be put in place before you must let traffic pass. Odds are, a malicious attacker will eventually bypass detection based on the fact that there are hackers out there with a rack of all the latest vendor IPS, Firewalls, etc. in a lab designed to test how effective a piece of malware is against any enterprise security solution. So in a nutshell, you will only be able to stop the majority of attacks launched against your network. Something will eventually get through. This means detecting and preventing can’t be your only security strategy.
This “already compromised” concept has increase demand for insider threat technology based on reacting to having your network breached. Post compromise technology is extremely important but obviously not where you want to end up regarding your security posture. The other area of focus growing in popularity besides blocking active attacks is identifying the ATTACKERS to prevent the initial attack aka BEFORE an attack or pre-attack. The concept is simple, why let yourself be attacked from a known malicious source? Why waste defense cycles blocking the same thing over and over again? Why access a source that has harmed many other users? Just block those pre-connection.
The “attacker” concept can be explained as web sources that may attack you if a connection is capable. This can be accessing malicious websites, hackers attacking you from untrusted networks such as an unregistered IP address or even trusted sources that are hacked and used as a pivoting point to launch attacks. Examples are clicking an email linked to a phishing server, searching the web for free software laced with trojans, logging into cloned trusted sources such as a fake Facebook login, Botnets phoning home from compromised systems and so on. All are bad and could be block pre-connection with the right research.
Developing security to block attackers is based on security research similar to how content filters categorize websites (example tagging pokerstar.com as “gambling”). Each website is given a level of trust just like how financial organizations grade people on credit score. Multiple factors are considered when grading a website’s trust such as how long the source has been on the Internet, where its located, the type of content, IP address, activity, and so on. For example, a “banking website” that has only been online for 3 days, based out of Russia but advertises itself as an America bank and targeting a ton of traffic at a particular range of IP addresses would set off a ton of red flags.
The attacker and attack defense concept should compliment one other. A example of the benefit from this can be compared against recent breaches of trusted sources such as what happened with Yahoo (breach info found here). Yahoo was fine however advertisement within Yahoo got compromised and attacked users. In this situation, the first handful of users would rely on an IPS or anti-virus to detect an attack. An ideal situation would be as attacks are seen, that data is shared on the cloud so others can avoid such attacks. Security products should be able to see “I’m being attacked” data and eventually blacklist the source before future systems have the ability to connect to that compromised source. Users that are attacked should eventually rely on blacklisting rather than continuously blocking the same attacks. Security researchers should attempt to contact the blacklisted source to indicate they are compromised and will remain blocked until they remediate the malicious activity.
Here is an example of testing the reputation concept. If you go to IHaveABadReputation.com, you will see the image below. Hypothetically, your system would see an attack, which you could prevent with a attack detection tool but you may also get compromised. This is a risky situation.
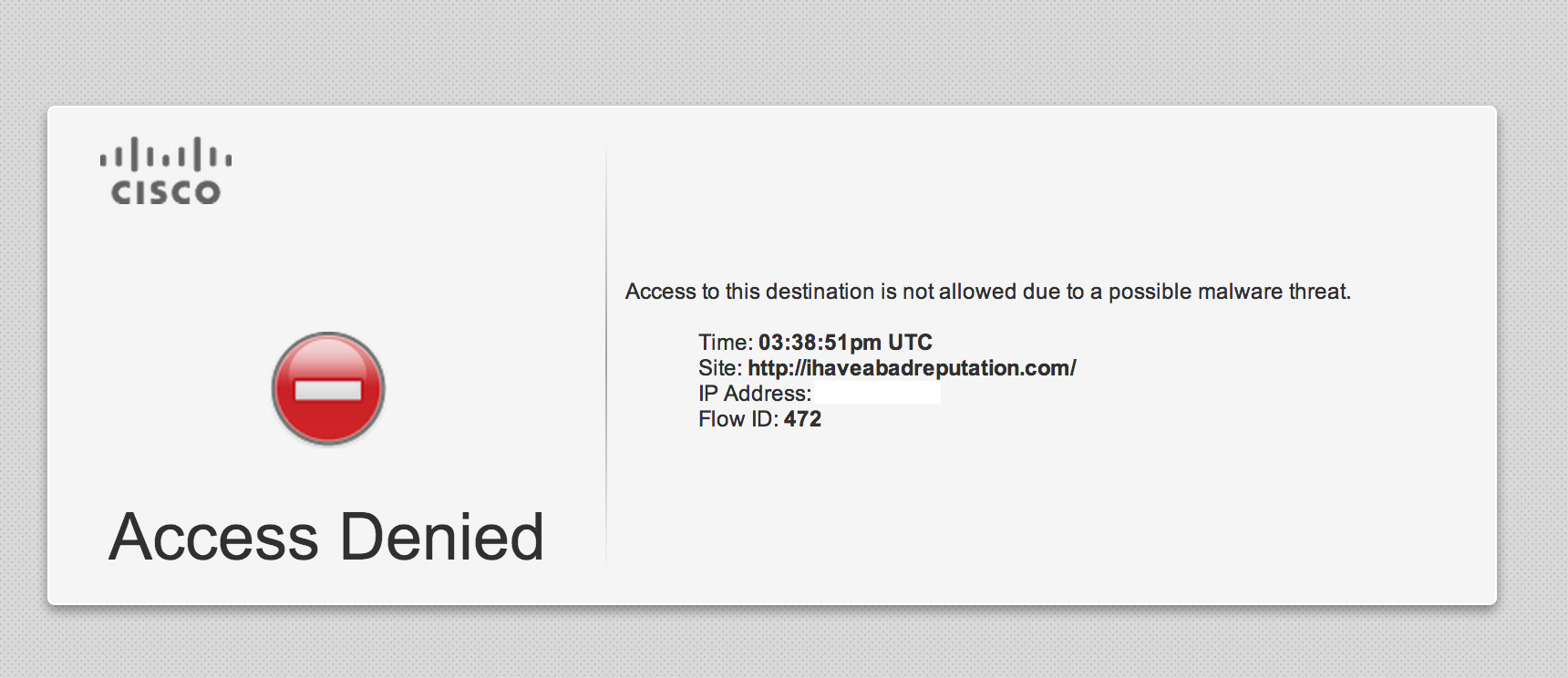
Having technology that blocks a website before it attacks you could look like the image below (using a Cisco branded solution). The idea is the security product doesn’t have to leverage any resources or have the latest signatures to prevent attacks since the connection is dropped at the doorway.
Yes I work for Cisco and showing one version of this concept but I believe this is the future of security for all vendors. The term “Next Generation” in relation to security to me means moving beyond an appliance to a cloud based global defense. This means sharing near real-time security data to help monitor the entire network for attackers and stop threats before they actually attack you. This way precious systems cycles can be used for attacks that get through your attacker defenses giving you more room for on box capabilities without sacrificing too much processing power.
Unfortunately many vendors don’t share attacker intelligence like they do with signature-based technology. You will find vendors advertising new hashes to attacks with many open source references however there is limited data for blacklisted sources that keep up with the real threats. This level of security research usually comes with a price tag and not something you can actually see meaning the research characteristics are typically company confidential. This especially applies to using data from live customer networks.
Hopefully one day attacker data will become a open source standard so everybody can benefit from pre-attack security capabilities. Imagine a global database monitoring all endpoint Anti-Virus, Network IPS and Firewall vendor data from customers and attack research. That would dramatically increase the time of detection for most attacks blocking attackers pre-connection.